Authentication keys for SSH, biometric authentication, and single sign-on (SSO) are exemplary alternatives that bolster security and enhance user convenience.
Update: March 4th 2024: While the guidance below – originally provided in 2013 – emphasizes the creation and management of secure passwords, more than a decade later, it’s important to recognize and advocate for the use of passwordless authentication methods wherever feasible.
For SSH access, the utilization of authentication keys coupled with the deactivation of password authentication (by setting PasswordAuthentication no in your SSHD configuration file) is advised.
- Enhanced Security: By eliminating passwords, you reduce the risk associated with password theft, phishing attacks, and brute-force attempts. Authentication keys and biometrics are considerably harder for malicious actors to compromise.
- Improved User Experience: Users no longer need to remember complex passwords or undergo frequent password resets, streamlining access and reducing support requests related to password issues.
- Simplified Management: For administrators, passwordless systems can simplify user management and security protocols, as there’s no need to enforce password policies or manage password databases.
Recommended urandom
Passwordless authentication methods offer several compelling advantages:
< /dev/urandom tr -dc ‘12345!@#$%qwertQWERTasdfgASDFGzxcvbZXCVB’ | head -c16;echo;
spw(){ < /dev/urandom tr -dc ‘[:graph:]’ | head -c16;echo; }
By fostering an environment that values advanced security measures over traditional password-dependent methods, we can pave the way for a more secure and user-friendly digital world.
It would take trillions of years to crack your password using these methods. This is why a strong password is essential.
With pass, each password lives inside a gpg encrypted file whose filename is the title of the website or resource that requires the password. These encrypted files may be organized into meaningful folder hierarchies, copied from computer to computer, and, in general, manipulated using standard command-line file management utilities. Thus, pass is also a command-line password manager.
spw(){ insert one of the above options here }
Also, remember, you should have security to avoid brute force password cracking. For example, after five failed attempts, the IP should be blocked and reported (for example, abuseipdb.com).
Generating secure passwords
spw
pwgen is widely available across Linux distributions and can typically be installed via the system’s package manager, using commands like apt install pwgen or dnf install pwgen. Read more about pwgen.
< /dev/urandom tr -dc ‘67890^*_+-=;:,.?yuiopYUIOPhjklHJKLbnmBNM’ | head -c16;echo;
For selecting secure passwords, here’s what is recommended:
This is an updated article from 2013. Here’s the previous method from the original article…
In the broader landscape of cybersecurity, moving towards passwordless authentication represents a forward-thinking approach that aligns with evolving security standards and user expectations.
Similarly, for MySQL, implementing setting skip-networking andbind-address = 127.0.0.1, alongside leveraging iptables to block or restrict port 3306 to designated IP addresses, enhances security. Direct socket connections are recommended for local MySQL communication if the database resides on the same server.
< /dev/urandom tr -dc ‘[:graph:]’ | head -c16;echo;
Published: November 23rd, 2013 | Last updated: March 4th, 2024
Using ‘pass’ to generate a secure password
Here’s my go-to command-line method for secure password generation. The command I use is:
While not all systems and services support passwordless options today, prioritizing these methods, where available, can significantly enhance the overall security posture of your server environments and user ecosystems.
Edit your bashrc
Despite the broad spectrum of security practices available, the importance of secure passwords is frequently overlooked, yet it remains a cornerstone of a fortified server environment.
pwgen -y 32
A common misconception is that all server aspects, including SSH and MySQL root passwords, require remote password access for security. However, if your commitment to security is unwavering, these components should be configured to eschew remote password login entirely.

Use the urandom command to generate secure passwords
While the focus on tools like pwgen and pass is useful, it’s crucial to remember that password strength is just one facet of server security. Implementing measures to thwart brute-force attacks, such as IP blocking after consecutive failed login attempts, complements the use of strong passwords.
As threats evolve with increasing sophistication, the commitment to adopting and integrating advanced security practices, especially passwordless options, becomes crucial.
System administrators are often tasked with the crucial role of establishing and reinforcing server safeguards. This encompasses various tasks, from deploying new servers to enhancing the security of existing ones, with a particular focus on creating robust passwords for various services such as SFTP and administrative panels.
source ~/.bash_profile
Other Linux commands use OpenSSL, dd, and date to generate passwords, but urandom pwgen is my preferred method. Feel free to add your methods below.
vi ~/.bashrc
Also, read the article Passwordless Authentication Services.
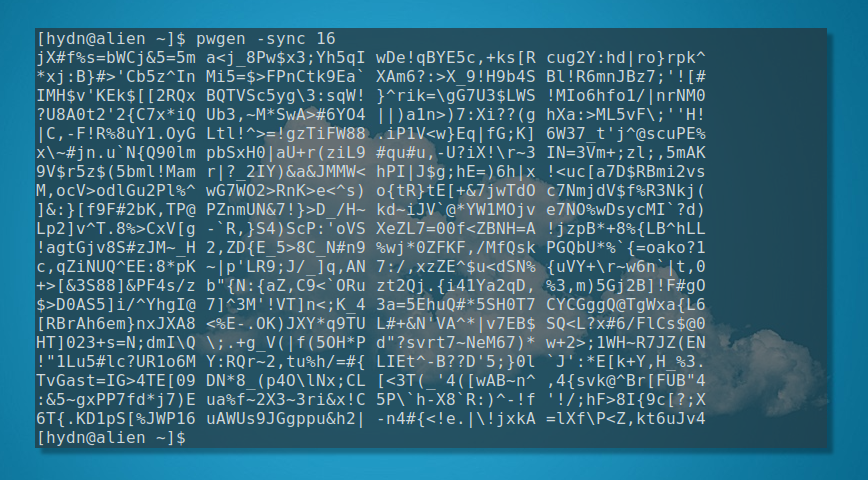
Need fewer generated passwords? Use pwgen -sync 16 1 where 1 = the number of password results.
Conclusion
Table of Contents
Once installed, here’s an explanation of the command I’m using above. You can fine-tune it to meet your needs:
For passwords that are secure but shorter use pwgen -sync 16, can be beneficial. It’s not recommended to create passwords shorter than 16 characters.