Recently, I wanted to test network throughput via command line with at least 3 tools. For the life of me, I could not remember iperf. Not being able to remember previously used command line tools is frustrating and something we can all relate to. So I created a go-to list of network tools for myself. Then, I thought, why not turn this list into a blog post? So I spent another hour or two compiling this ongoing list of Linux Networking Commands and Scripts. I look forward mostly to suggestions, because I know there’s always something missing or new scripts out there to try.
Table of Contents
Linux Networking commands and scripts
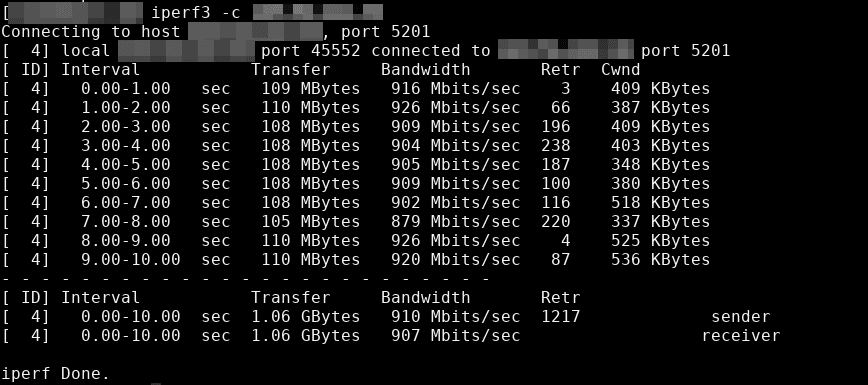
iperf command example/screenshot
This list of Linux Networking commands and scripts will receive ongoing updates:
- aria2 – downloading just about everything. Torrents included.
- arpwatch – Ethernet Activity Monitor.
- bmon – bandwidth monitor and rate estimator.
- bwm-ng – live network bandwidth monitor.
- curl – transferring data with URLs. (or try httpie)
- darkstat – captures network traffic, usage statistics.
- dhclient – Dynamic Host Configuration Protocol Client
- dig – query DNS servers for information and obtain various types of DNS records.
- dstat – replacement for vmstat, iostat, mpstat, netstat and ifstat.
- ethtool – utility for controlling network drivers and hardware.
- gated – gateway routing daemon.
- host – DNS lookup utility.
- hping – TCP/IP packet assembler/analyzer.
- ibmonitor – shows bandwidth and total data transferred.
- ifstat – report network interfaces bandwidth.
- iftop – display bandwidth usage.
- ifconfig command – manage network interfaces, display information, and configure settings. Historically significant in system administration.
- ip (PDF file) – a command with more features that ifconfig (net-tools).
- iperf3 – network bandwidth measurement tool. (above screenshot Stacklinux VPS)
- iproute2 – collection of utilities for controlling TCP/IP.
- iptables – take control of network traffic.
- IPTraf – An IP Network Monitor.
- iputils – set of small useful utilities for Linux networking.
- iw – a new nl80211 based CLI configuration utility for wireless devices.
- jwhois (whois) – client for the whois service.
- “lsof -i” – reveal information about your network sockets.
- mtr – network diagnostic tool.
- net-tools – utilities include: arp, hostname, ifconfig, netstat, rarp, route, plipconfig, slattach, mii-tool, iptunnel and ipmaddr.
- ncat – improved re-implementation of the venerable netcat.
- netcat – networking utility for reading/writing network connections.
- nethogs – a small ‘net top’ tool.
- Netperf – Network bandwidth Testing.
- netplan – Netplan is a utility for easily configuring networking on a linux system.
- netsniff-ng – Swiss army knife for daily Linux network plumbing.
- netstat command – provides network statistics, routing tables, and connection information. Part of net-tools, now largely replaced by the ‘ss command’.
- netwatch – monitoring Network Connections.
- ngrep – grep applied to the network layer.
- nload – display network usage.
- nmap – network discovery and security auditing.
- nmcli – a command-line tool for controlling NetworkManager and reporting network status.
- nmtui – provides a text interface to configure networking by controlling NetworkManager.
- nslookup – query Internet name servers interactively.
- ping – send icmp echo_request to network hosts.
- route – show / manipulate the IP routing table.
- slurm – network load monitor.
- snort – Network Intrusion Detection and Prevention System.
- smokeping – keeps track of your network latency.
- socat – establishes two bidirectional byte streams and transfers data between them.
- speedometer – Measure and display the rate of data across a network.
- speedtest-cli – test internet bandwidth using speedtest.net
- ss – utility to investigate sockets.
- ssh – secure system administration and file transfers over insecure networks.
- tcpdump – command-line packet analyzer.
- tcptrack – Displays information about tcp connections on a network interface.
- telnet – user interface to the TELNET protocol.
- tracepath – very similar function to traceroute.
- traceroute – print the route packets trace to network host.
- vnStat – network traffic monitor.
- websocat – Connection forwarder from/to web sockets to/from usual sockets, in style of socat.
- wget – retrieving files using HTTP, HTTPS, FTP and FTPS.
- Wireless Tools for Linux – includes iwconfig, iwlist, iwspy, iwpriv and ifrename.
- Wireshark – network protocol analyzer.
- Suggestions welcomed.
Read also:
Network Fundamentals
Understanding network fundamentals is crucial for anyone working with computer networks. These basics form the backbone of all networking activities and include several key components:
- Network Protocols: These are the rules and standards that govern data transmission over a network. Common protocols include TCP/IP, which ensures reliable communication, HTTP for web traffic, and FTP for file transfers.
- Network Topologies: This refers to the physical and logical arrangement of devices on a network. Examples include bus, star, and ring topologies, each with its own advantages and use cases.
- Network Devices: These are the hardware components that make up a network, such as routers, switches, and firewalls. Each device plays a specific role in managing and directing network traffic.
- Network Media: This includes the physical materials used to transmit data, such as copper cables, fiber optic cables, and wireless signals. The choice of media affects the speed and reliability of the network.
By grasping these fundamentals, you lay a solid foundation for more advanced networking concepts and technologies, enabling you to build, manage, and troubleshoot networks effectively.
Network Connectivity
Network connectivity is the lifeline of any network, enabling devices to communicate and share resources. There are several ways to achieve network connectivity:
- Wired Connections: These use physical cables, such as Ethernet, to connect devices. Wired connections are known for their reliability and speed, making them ideal for stable, high-speed network environments.
- Wireless Connections: These use wireless signals, such as Wi-Fi, to connect devices. Wireless connections offer flexibility and mobility, allowing devices to connect without the constraints of physical cables.
- Virtual Private Networks (VPNs): VPNs use encryption and other security measures to create secure, private connections over public networks. This is essential for protecting sensitive data and ensuring privacy when accessing remote networks.
Network connectivity is essential for various applications, including:
- Internet Access: Connecting to the global network of interconnected computers to access online resources.
- File Sharing: Allowing devices to share files and data over a network.
- Communication: Enabling real-time communication through email, instant messaging, and video conferencing.
Understanding and managing network connectivity ensures that devices can communicate efficiently and securely.
IP Addresses and DNS
IP addresses and DNS (Domain Name System) are fundamental to network connectivity, enabling devices to locate and communicate with each other:
- IP Addresses: These are unique numerical addresses assigned to each device on a network. They serve as identifiers, allowing devices to send and receive data accurately. There are two types of IP addresses: IPv4 and IPv6, with IPv6 providing a larger address space.
- DNS: This system translates human-readable domain names (like www.example.com) into IP addresses. This translation is crucial because while humans find domain names easier to remember, computers use IP addresses to route data.
When you enter a domain name into a web browser, the DNS system translates it into an IP address, directing your request to the correct server. This seamless translation is what makes browsing the internet intuitive and user-friendly.
Network Information and Statistics
Monitoring network performance is essential for maintaining a healthy and efficient network. Key metrics include:
- Network Traffic: This refers to the amount of data being transmitted over a network at any given time. Monitoring traffic helps identify congestion and optimize bandwidth usage.
- Network Latency: This is the delay between sending and receiving data. High latency can affect the performance of real-time applications like video conferencing and online gaming.
- Network Packet Loss: This measures the number of data packets lost during transmission. High packet loss can indicate network issues that need to be addressed.
- Network Throughput: This is the rate at which data is successfully transmitted over a network. It is a critical measure of network performance and capacity.
By analyzing these metrics, network administrators can gain insights into network performance, identify potential issues, and take corrective actions to ensure smooth and efficient network operations.
Essential Linux Network Commands
Linux offers a robust set of commands for managing and troubleshooting network connections. Some essential Linux network commands include:
- ifconfig: Used to configure and manage network interfaces. It allows you to assign IP addresses, enable or disable interfaces, and more.
- ip: A versatile command for managing IP addresses and routing tables. It provides more features than ifconfig and is preferred for modern network configurations.
- ping: Used to test network connectivity by sending ICMP echo requests to a host. It helps diagnose network issues by measuring round-trip time and packet loss.
- traceroute: Traces the path of data packets to a network host, showing each hop along the way. It is useful for identifying where delays or failures occur in the network.
- netstat: Displays network statistics and connections, providing insights into active connections, routing tables, and interface statistics.
These commands are indispensable for anyone working with Linux networks, offering powerful tools to configure, manage, and troubleshoot network connections effectively.
Network Security
Network security is vital for protecting networks from unauthorized access and cyber threats. Key measures include:
- Firewalls: These devices control incoming and outgoing network traffic based on security rules, acting as a barrier between trusted and untrusted networks.
- Encryption: Converts plaintext data into unreadable ciphertext, protecting it from unauthorized access during transmission.
- Access Control: Measures that determine who can access the network and what actions they can perform, ensuring that only authorized users can interact with network resources.
- Intrusion Detection and Prevention Systems (IDPS): These systems monitor network traffic for signs of unauthorized access or malicious activity, helping to detect and prevent security breaches.
Implementing robust network security measures is essential for safeguarding sensitive data and maintaining the integrity and availability of network resources. By protecting against potential threats, organizations can ensure the security and reliability of their networks.
Published: January 31st, 2020 | Last updated: November 10th, 2024