Linux server security is of critical importance to sysadmins. One central part of keeping Linux servers secure is by installing security updates promptly. Too often, there are compromised servers on the internet due to pending security updates waiting for a manual update. On both Ubuntu and Debian, the unattended-upgrades package can be configured to perform unattended-upgrades to install updated packages and security updates automatically.
In general, on critical servers where you cannot afford unplanned downtime should be prudent with unattended-upgrades (or automatic updates). In general, on critical servers where you cannot afford unplanned downtime, you should be prudent with unattended-upgrades (or automatic updates). While there are reasons to be cautious, it is also worth considering.
Table of Contents
Advantages of Automatic Updates
Automatic updates provide significant advantages for maintaining server security and operational efficiency.
First and foremost, they enhance security by ensuring that security patches are applied as soon as they become available, effectively minimizing the window of vulnerability to potential threats. This proactive approach significantly reduces the risk of exploitation by malicious actors.
Additionally, automatic updates offer substantial time efficiency by saving administrators from the manual task of constantly monitoring and installing updates. This allows them to focus on other critical tasks and strategic initiatives, thereby improving overall productivity.
Furthermore, automatic updates ensure consistency across all servers in the infrastructure, as they receive the necessary updates promptly and uniformly. This consistency reduces the risk of discrepancies and potential conflicts between different server versions, leading to a more stable and reliable server environment.
Install unattended-upgrades
As of Debian 9, both the unattended-upgrades and apt-listchanges packages are installed by default. Recent releases of Ubuntu also come with unattended-upgrades installed by default. To install the unattended-upgrades package, enter the following in your terminal:
sudo apt update && sudo apt upgrade sudo apt install unattended-upgrades
Remember, you’ll want to monitor updates and changes to your Linux server over time. You can monitor via /var/log/dpkg.log or read the log files in /var/log/unattended-upgrades/. You can also monitor changes by installing the apt-listchanges package (optional).
sudo apt install apt-listchanges
The apt-listchanges can be configured to send emails about update changes. apt-listchanges is a tool to show what has been changed in a new version of a Debian package compared to the version currently installed on the system. It does this by extracting the relevant entries from the NEWS.Debian and changelog[.Debian] files, usually found in /usr/share/doc/package, from Debian package archives. On both Debian and Ubuntu, as Ubuntu is a derivative of Debian.
Configure unattended-upgrades
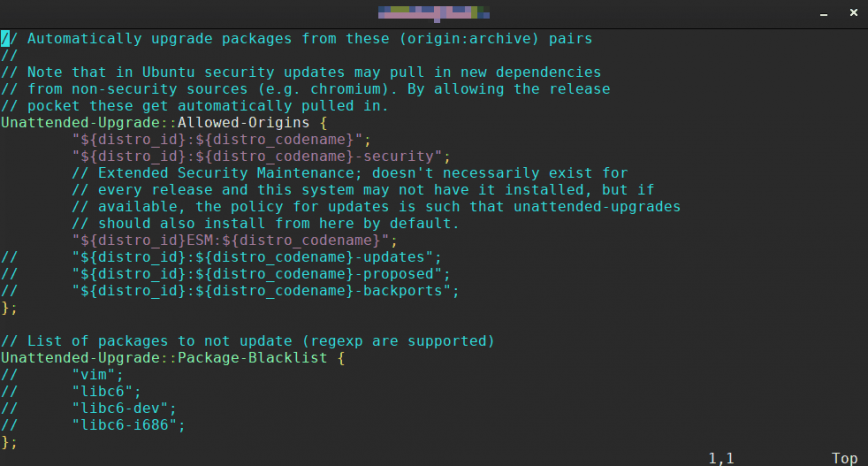
The unattended-upgrades config file location is /etc/apt/apt.conf.d/50unattended-upgrades.
Lines starting with a double slash // have no effect. Therefore, to “enable” a line, remove the double slash //.
Selecting what to update
The section that controls what packages are updated automatically starts with Unattended-Upgrade::Allowed-Origins {. It will look something like the above screenshot. You can enable all packages or security updates only. By default, it will only install security updates. To enable updates from other repositories, uncomment the repository by removing the double slash // from the start of the line. Example:
"${distro_id}:${distro_codename}-updates";
Here are some details on the update types available, as explained by Ubuntu:
“${distro_id}:${distro_codename}-security”; – Auto updating security updates will patch holes and vulnerabilities on your server.
“${distro_id}:${distro_codename}-updates”; – Updates (aka Recommended Updates) contain non-critical updates which can remove major annoyances and broken packages but which do not affect your security. Other than fixing some, they do not enable any features. Enabling this is generally a good idea. The amount to download as well as the changes are not too big, but it improves your server stability in various ways.
“${distro_id}:${distro_codename}-proposed”; – The proposed updates are updates that are waiting to be moved into the recommended updates queue after some testing. They may never reach recommended, or they may be replaced with a more recent update. Enabling this is reasonable if you want to participate in testing minor updates or know that your specific problem has been solved here, but the package hasn’t reached recommended yet. WARNING: Enabling the proposed updates repository can break your system. It is not recommended for inexperienced users.
“${distro_id}:${distro_codename}-backports”; – Backported updates are pieces of software that come from a newer major release. Thus, they can contain new features but may also break compatibility with their older version. However, they are compiled specifically for your version of Ubuntu. In effect, it saves you the hassle of broken dependencies and major downloads. Enabling this is reasonable if you want new features but don’t want your system to be unstable.
Enabling email reporting
Next, to enable email reporting. Find this line:
//Unattended-Upgrade::Mail "root";
Change it to:
Unattended-Upgrade::Mail "replacewithyouremail";
You can also leave it set to the default “root” to send email reports to the server’s root account. Here’s an example of unattended-upgrades mail config:
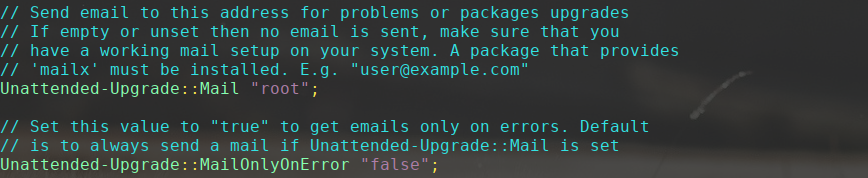
The remainder of the config file is self-explanatory. If you have any questions, post them below.
Configure update frequency
By default, unattended upgrades will install available updates daily. To confirm, take a look at the config file: /etc/apt/apt.conf.d/20auto-upgrades. It should look like this:
APT::Periodic::Update-Package-Lists "1"; APT::Periodic::Unattended-Upgrade "1";
APT::Periodic::Update-Package-Lists – allows you to specify the frequency (in days) at which the package lists are refreshed.
APT::Periodic::Unattended-Upgrade – When enabled, the daily script will execute unattended-upgrade.
APT::Periodic::Download-Upgradeable-Packages – Frequency (in days) for the downloading of the actual packages.
APT::Periodic::AutocleanInterval – It controls how often obsolete packages are removed from the APT cache. This keeps the APT cache at a reasonable size and means that you don’t need to worry about that task.
Sample config: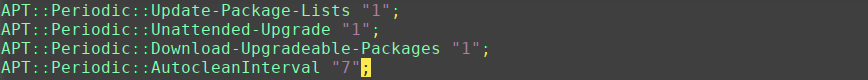
The above configuration will update package lists, download packages, and install available upgrades daily. At the same time, APT cache will be cleaned every 7 days.
Test unattended-upgrades
You can test your config with a dry run. Use the following command. Refer to the man page for help:
sudo unattended-upgrades --dry-run --debug
Conclusion
By enabling Unattended Upgrades (Automatic Updates) on Ubuntu or Debian servers, you’ve taken an important step to protect your server from vulnerabilities. Manually updating the system and applying patches can be a very time-consuming process. Unattended Upgrades save a lot of time. However, for many servers and/or VMs, I would recommend using bulk automation tools such as Ansible, Salt, Chef, Puppet, etc. Automatic updates are also available on Red Hat, CentOS and Fedora Linux. I will post a how-to article about this next.