To address this limitation, the Drush Firewall module includes a special file that makes sure certain commands are handled properly and safely. The file also applies extra layers of protection against unwanted changes.Among other things, this means disabling the Firewall in some core commands and safeguarding your website from the risks associated with running commands like ‘sql:sync.’ The ‘sql:sync’ command is typically used to synchronize databases between Drupal environments (like from a production environment to a development environment). It can overwrite the target database with the source database’s data and structure. Running ‘sql:sync’ in certain scenarios may pose risks. For example, syncing a production database with a development database could lead to losing data or compromising sensitive information.
Today, we’d like to explore a new Drupal module that covers an essential but sometimes overlooked aspect of keeping websites safe. It’s about protecting them from unwanted changes or issues that might be caused by running certain commands in Drush. With special pride, we want to emphasize that the module’s creator is Bryan Sharpe of our team who is a prominent contributor to drupal.org.
To add the module to the Drush configuration, which will take care of the handling of no-bootstrap commands and provide extra protection against commands like ‘sql:sync’ as described in an earlier chapter, follow these steps:
A glimpse at Drush: the power of the command line
In some cases, you might really need to run a command, even if it has been configured to be denied in the Drush Firewall. So the module provides you with a special way to bypass its restrictions in the command line, which we’ll show in more detail in the “how-to” chapter.
When Drush prepares to run a command, it starts by bootstrapping the Drupal environment. Some Drush commands do not bootstrap Drupal, which means they don’t go through the entire Drupal initialization process, including loading all modules and configurations. Unfortunately, these no-bootstrap commands cannot be directly executed from within the Drush Firewall module.
Commands suitable for the development environment might be harmful on a live website, and the maintenance mode has its specifics, too. Taking into account different environmental conditions, the Drush Firewall module enables you to configure the denied/allowed commands in three modes:
By adding the Drush Firewall module to your Drush configuration file — for which we’ll provide further instructions — you enable this extra protection for dealing with specific Drush commands.
Drush vs. Composer: rivals or colleagues?
It needs to be noted that even after the arrival of Composer, Drush still plays a role in the realm of module management, too. For example, in cases when a new module version requires database schema changes, Composer installs the module, but Drush steps in to execute the necessary database updates.
Authored by Nadiia Nykolaichuk and Bryan Sharpe.
By typing one simple command, you can initiate huge processes that would otherwise require repetitive manual actions in the Drupal admin UI or writing custom scripts. Memorizing the most needed commands doesn’t take much time, and once you do, Drush becomes your powerful ally, ensuring significant time savings. However, the power of Drush needs to be “tamed” sometimes for the sake of the website’s security, and we’ll discuss it in more detail below.
The Drush Firewall module: what it does and why it matters
The name of the module — Drush Firewall — pretty much speaks for itself because the word “firewall” is associated with a reliable tool that acts as a shield for ultimate protection. To be more specific, the Drush Firewall module enables you to control and manage which Drush commands can or cannot be executed based on different environmental conditions. The module is brand new and currently at its alpha stage.
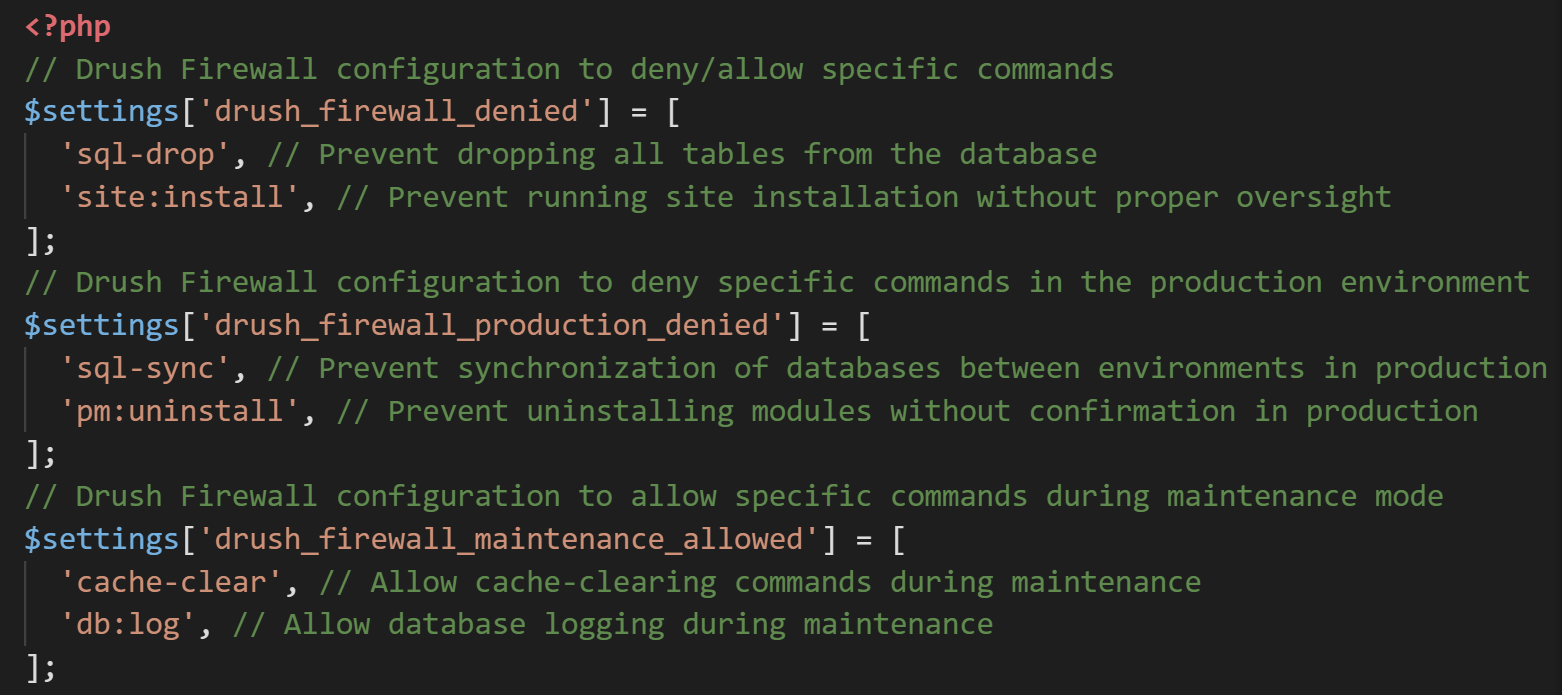
// Drush Firewall configuration to deny specific commands
$settings['drush_firewall_denied'] = [
'sql-drop', // Prevent dropping all tables from the database
'site:install', // Prevent running site installation without proper oversight
];
As a result, Drush’s role shifted to focusing more on website administration and automation tasks such as cache clearing, database updates, or configuration management. While Composer handles dependency management and updates, Drush complements it by providing essential administrative capabilities.
Three modes for different environmental conditions
To perform its mission, Drush provides an extensive set of simple command-line instructions. Examples of popular Drush commands include ‘drush cr’ for rebuilding caches, ‘drush updatedb’ (or ‘drush updb’ for short) for updating the database, ‘drush pm-enable’ for enabling modules, and others.
- Across all environments (global settings). You can specify the commands that will never be allowed to run.
- In the production environment. You can list the commands that will be denied on a live website.
- In the maintenance mode. You can decide which commands to allow during maintenance mode.
Some examples of Drush commands that might need caution
- The ‘drush sql-drop’ command should be used with extreme care as it poses a significant risk. The command drops all tables from the Drupal database, essentially performing a factory reset and erasing all data.
- Automated Cron, which is Drupal’s system for running scheduled tasks on the website automatically, can be managed and triggered via commands like ‘drush cron.’ When an environment is in maintenance mode (like during critical updates or deployments), running Cron is unwanted. For example, there is an issue on drupal.org discussing that Cron should not run when you’re updating your Drupal site using update.php because it might conflict with the update process, leading to updates not applying correctly or other inconsistencies.
- While uninstalling modules is a common task, using the ‘drush pm-uninstall’ command can remove a module and its data from the website without confirmation. If not used carefully, it can lead to unintentional removal of important functionality.
- The ‘config-set’ command allows changing configuration settings for the Drupal website. While useful for managing configurations, incorrect changes could break the website or lead to unexpected behavior.
- The ‘entity-delete’ command allows the deleting of entities from the Drupal website, such as nodes, users, or taxonomy terms. Careless use of this command can result in the loss of important content.
- During cache rebuild, the site might respond more slowly to user requests until the caches are fully rebuilt. So the ‘cache:rebuild’ command, when run on a live production site during peak traffic, might lead to heavy resource usage and potential performance impact. Still, this command might be necessary, so if you’re disabling it, you can use the ‘–disable-firewall’ argument to bypass the Firewall as we’ll describe later.
Here are the settings examples for all the three configuration modes:
The handling of no-bootstrap commands and extra protection
drush:
include:
- '/var/www/your-drupal-website/modules/contrib/drush_firewall'
How to disable the Drush Firewall
By restricting commands that could have unplanned and undesirable consequences, Drush Firewall reduces the risk of data loss, functionality removal, site downtime, sensitive information disclosure, or other issues.
// Drush Firewall configuration to deny specific commands in the production environment
$settings['drush_firewall_production_denied'] = [
'sql-sync', // Prevent synchronization of databases between environments in production
'pm:uninstall', // Prevent uninstalling modules without confirmation in production
];
With the help of Drush Firewall, you can ensure that command-line operations are handled appropriately, preventing unintended, accidental, or unauthorized actions. It provides an automated approach to command-line security, giving developers and administrators more confidence and peace of mind.
The option to disable the Drush Firewall
1) Overall command denial. Use ‘$settings[‘drush_firewall_denied’] = [ ];’ to list the commands that should never be allowed to run:
Step-by-step guide to configuring the Drush Firewall module
How to deny/allow certain Drush commands
- Install the Drush Firewall module per normal and enable it on your Drupal website.
- Navigate to your Drupal installation directory and locate the settings.php file within the sites/default directory. It’s always a good idea to do a backup of the file before making changes.
- Open the settings.php file using an editor of your choice.
- List your Drush commands in the file after the initial $settings array declaration. Make sure to maintain proper PHP syntax and spacing as in the snippets below. Each setting should be separated by a comma.
- Optionally, you might consider adding comments to provide more context for the commands.
It’s essential to have website backups in place before executing any critical Drush commands, and leveraging the capabilities of the Drush Firewall module can further increase website security and stability.
// Drush Firewall configuration to allow specific commands during maintenance mode
$settings['drush_firewall_maintenance_allowed'] = [
'cache-clear', // Allow cache-clearing commands during maintenance
'db:log', // Allow database logging during maintenance
];
drush –disable-firewall cache-rebuild
Drush empowers Drupal developers and administrators to perform an extremely wide range of operations, from clearing cache or running utilities like Cron to exporting site configuration or doing database updates. In June 2023, Drush 12 was released as the latest major version of the tool, introducing numerous enhancements.
Join us in this article as we uncover the significance of the Drush command-line shell and explain why protection against specific Drush commands, especially in certain scenarios, is important. And, of course, we’ll explain how the Drush Firewall module can help, and carefully walk you through the steps of configuring it for your website security.
How to add the module to your Drush configuration file
Before the introduction of Composer to the Drupal ecosystem, Drush was a large part of the module management process. However, Composer revolutionized the workflows by enabling developers to declare and manage dependencies for Drupal core and contributed modules in a standardized way.
- Navigate to your Drupal project’s root directory.
- Open the drush folder. If it doesn’t exist, create it.
- Inside the folder, locate the drush.yml file and open it in a text editor of your choice.
- Add the following lines to the file (the example below shows the path to a website located at /var/www/):
Drush, short for “Drupal Shell,” is a robust command line and scripting interface for Drupal websites. It is designed to streamline and facilitate day-to-day website management and development workflows.
Whether you’re performing routine website maintenance, actively developing new features, or managing a live production environment, the Drush Firewall module is your website’s reliable guard. You can fine-tune the module’s settings to meet your project’s needs and circumstances, striking the right balance between safety and efficiency. We are happy to support the development of game-changing tools like Drush Firewall that increase the security of websites across the Drupal community.
Final thoughts
Drupal boasts a variety of built-in and add-on tools to ensure website security, stability, and smooth operation. They fight spam bots, provide two-factor authentication, take care of database backups, and do many other important tasks. Each tool addresses website protection from a different perspective, and they are most effective when combined.