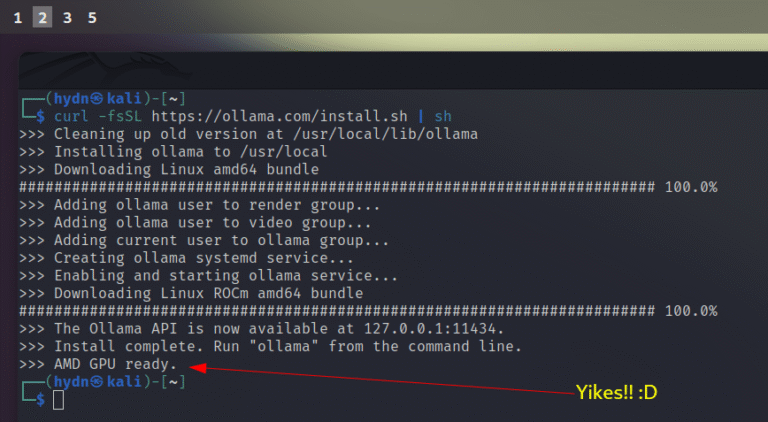
Service accounts are absent. So are API keys, tokens, and certificates. The most widely used playbook framework in enterprise security stops at human and device credentials. The organizations following it inherit that blind spot without realizing it.
Gartner’s ransomware preparation guidance, the April 2024 research note “How to Prepare for Ransomware Attacks” that enterprise security teams reference when building incident response procedures, specifically calls out the need to reset “impacted user/host credentials” during containment. The accompanying Ransomware Playbook Toolkit walks teams through four phases: containment, analysis, remediation, and recovery. The credential reset step instructs teams to ensure all affected user and device accounts are reset.
The most authoritative playbook framework has the same blind spot
CyberArk’s 2025 Identity Security Landscape puts numbers to the problem: 82 machine identities for every human in organizations worldwide. Forty-two percent of those machine identities have privileged or sensitive access.
The gap between ransomware threats and the defenses meant to stop them is getting worse, not better. Ivanti’s 2026 State of Cybersecurity Report found that the preparedness gap widened by an average of 10 points year over year across every threat category the firm tracks. Ransomware hit the widest spread: 63% of security professionals rate it a high or critical threat, but just 30% say they are “very prepared” to defend against it. That’s a 33-point gap, up from 29 points a year ago.
Gartner frames the urgency in terms few other sources match: “Ransomware is unlike any other security incident,” the research note states. “It puts affected organizations on a countdown timer. Any delay in the decision-making process introduces additional risk.” The same guidance emphasizes that recovery costs can amount to 10 times the ransom itself, and that ransomware is being deployed within one day of initial access in more than 50% of engagements. The clock is already running, but the containment procedures don’t match the urgency — not when the fastest-growing class of credentials goes unaddressed…
The same research note identifies the problem without connecting it to the solution. Gartner warns that “poor identity and access management (IAM) practices” remain a primary starting point for ransomware attacks, and that previously compromised credentials are being used to gain access through initial access brokers and dark web data dumps. In the recovery section, the guidance is explicit: updating or removing compromised credentials is essential because, without that step, the attacker will regain entry. Machine identities are IAM. Compromised service accounts are credentials. But the playbook’s containment procedures address neither.
By Louis Columbus
Read Full Article: VentureBeat