



One of the most crucial lessons I’ve learned as a CISO is that no single approach works for every organization. Each company operates in its own context, with its own set of challenges,…
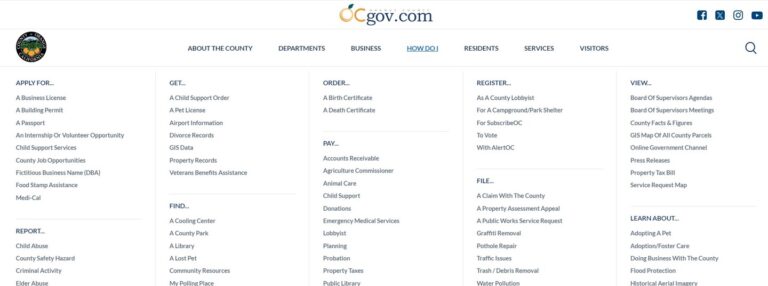
Government websites are critical in disseminating timely, accurate information to constituents during a crisis or emergency. Alerts such as the Sitewide Alert module make Drupal an ideal platform for government organizations looking to…

Modern irrigation robots are equipped with smart sensors that monitor soil moisture levels, weather conditions, and even grass health. This data allows the system to make informed decisions about when and how much…
Oct 31, 2025 Ariffud M. Summarize with: Most people transfer a domain to get better renewal pricing, consolidate services with their hosting provider, or escape poor customer support. To transfer your domain to…
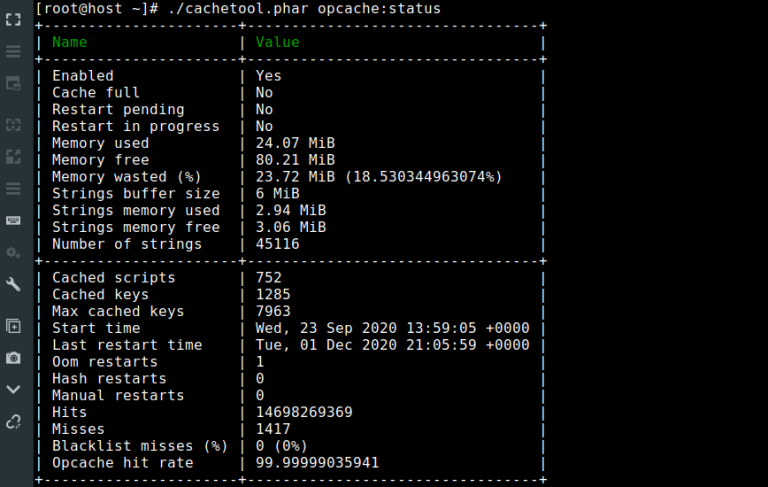
OPcache is a PHP extension that improves PHP performance by storing precompiled script bytecode in shared memory, thereby removing the need for PHP to load and parse scripts on each request. The extension…
Oct 24, 2025 Summarize with: The .eu domain is the official domain extension for businesses, organizations, and individuals based in the European Union (EU) and the European Economic Area (EEA). The main advantages…