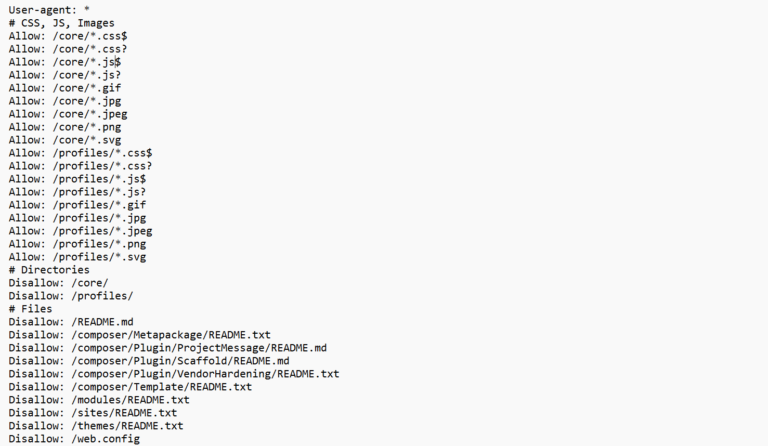
MCP vs A2A: The Hidden Exposure Layer Powering Agentic AI
Agentic AI can think, act, and share information independently. That’s enormously beneficial. But it’s also created a hidden exposure layer – one that isn’t obvious in logs or endpoints but can put systems,…