SSH command in Linux, with examples
This article is a follow-up to the previous 90 Linux Commands frequently used by Linux Sysadmins post. Every week, as time allows, I will publish articles on the 90 commands geared toward Linux sysadmins and…
This article is a follow-up to the previous 90 Linux Commands frequently used by Linux Sysadmins post. Every week, as time allows, I will publish articles on the 90 commands geared toward Linux sysadmins and…
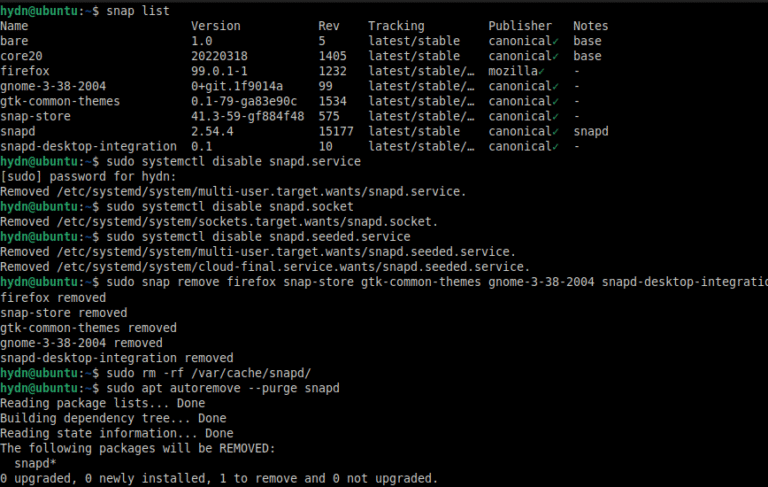
The first thing I did after installing Ubuntu 22.04 LTS was to remove Snap and its snap packages completely. I’m not proud of that approach, as I have nothing against snap packages per…
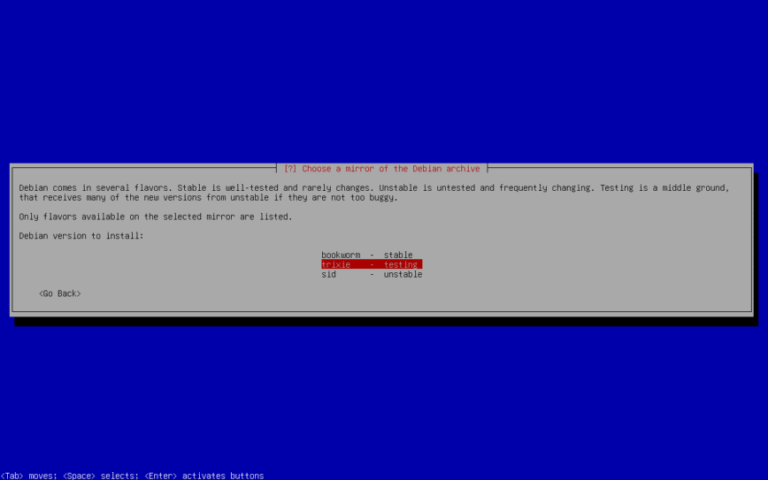
In my tech journey, I’ve always had an affinity for the cutting-edge, the not-fully-tested waters of the Linux world. Rolling release distributions like Arch, Fedora, or even a custom-installed Kali Linux have been…
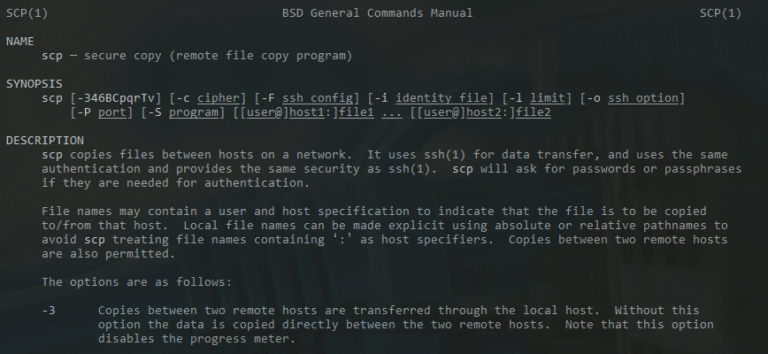
This post includes SCP examples. SCP or secure copy allows the secure transferring of files between a local host and a remote host or between two remote hosts. It uses the same authentication…
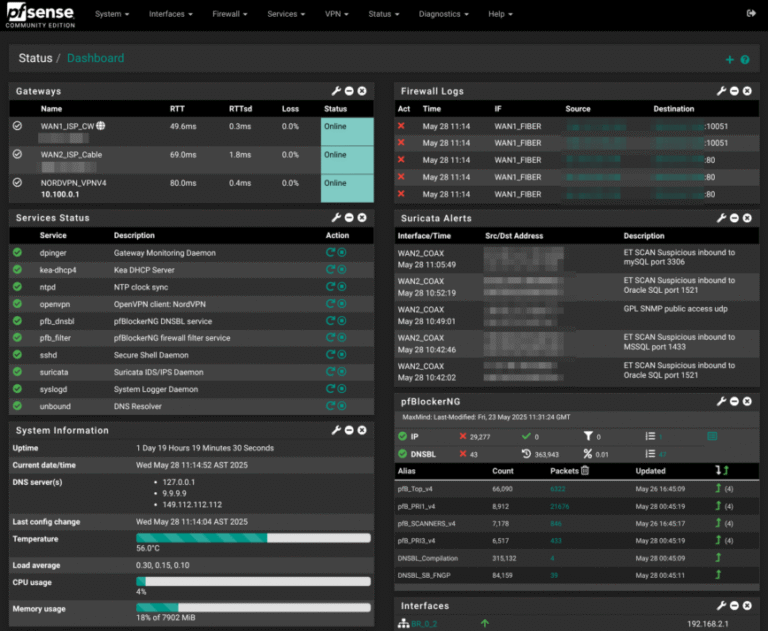
Let’s pick up right where Part 1 left off: pfSense Firewall Appliance Unboxing. This isn’t a quick-start guide. It’s my logbook from weeks of fine-tuning pfSense. Weeks, not years, so follow along and…

May 30, 2025 Ariffud M. 11min Read The LGTM stack – consisting of Loki for logs, Grafana for visualization, Tempo for tracing, and Mimir for metrics – is an open-source observability suite developed…

The sudo command in Linux is one of the most important and widely used commands for managing system permissions. It allows you to run a command as the superuser, giving you elevated privileges…
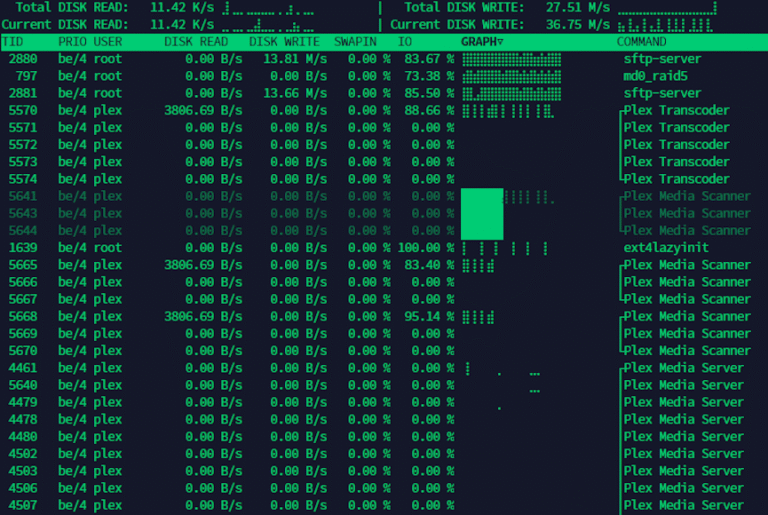
This iotop command guide follows my previous 90 Linux Commands frequently used by Linux Sysadmins article. As time allows, I will continue to publish articles on the 90+ commands geared toward Linux sysadmins…
May 22, 2025 10min Read Firebase provides comprehensive tools that help you develop and deploy applications more easily. It mainly streamlines the backend setup process by providing pre-configured services like databases and authentication…
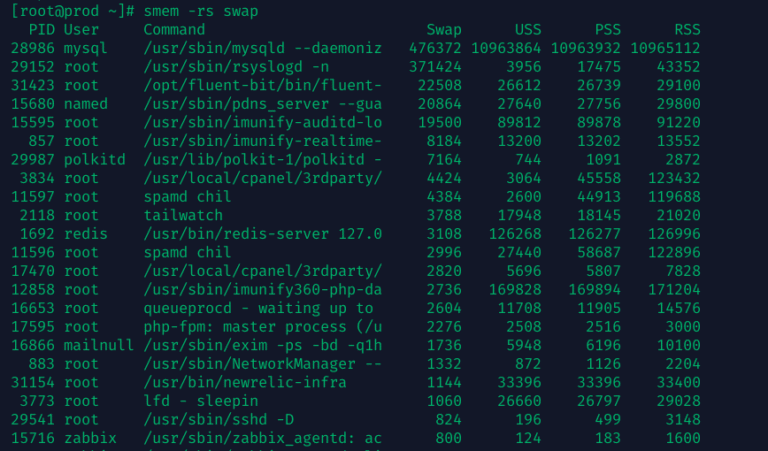
If you’ve ever looked at your server and wondered why it’s using swap even though plenty of RAM is available, you’re not alone. This is a common scenario on Linux systems, and it…

Recently, I supported a client with solving MySQL performance issues. There were several areas where MySQL performance issues were addressed. One issue, however, that was overlooked before our communications was that of keeping…

When it comes to database performance monitoring and optimization, MySQL offers a powerful tool called Performance Schema. This versatile instrument provides invaluable insights into the inner workings of your MySQL database, enabling you…
May 19, 2025 Viktoras D. Datapacks (or data packs) are a powerful way to customize Minecraft without mods. They expand gameplay in vanilla Minecraft, multiplayer, and existing singleplayer worlds. You can change game…

May 06, 2025 Once a niche effort, automation has now become a business priority. Not only does it streamline operations – it has also proven effective in improving product quality and even customer…
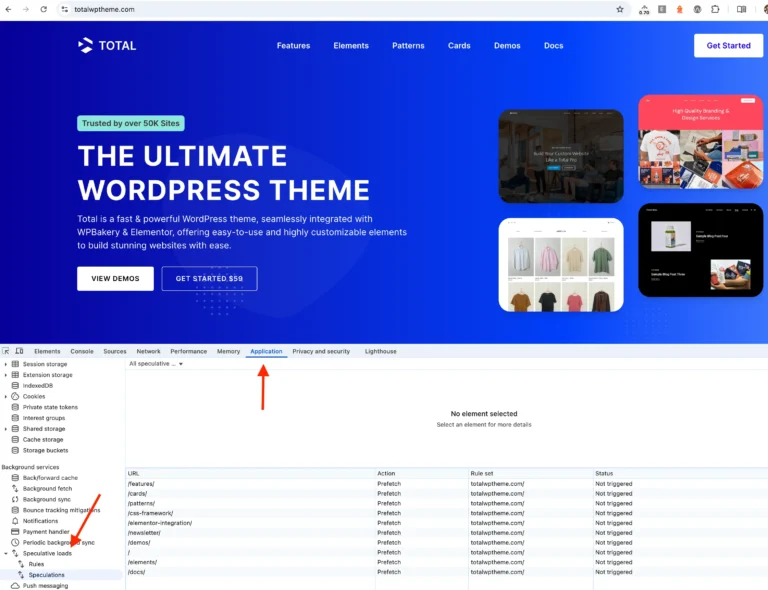
WordPress 6.8 introduced a highly requested feature: Speculative Loading. But what exactly is it, and how does it affect your website? In simple terms, and in WordPress specifically, it’s a technique that makes…
Apr 29, 2025 Matleena S. With so many different web hosting services to choose from, how do you decide which one is the best for your project? It all comes down to understanding…
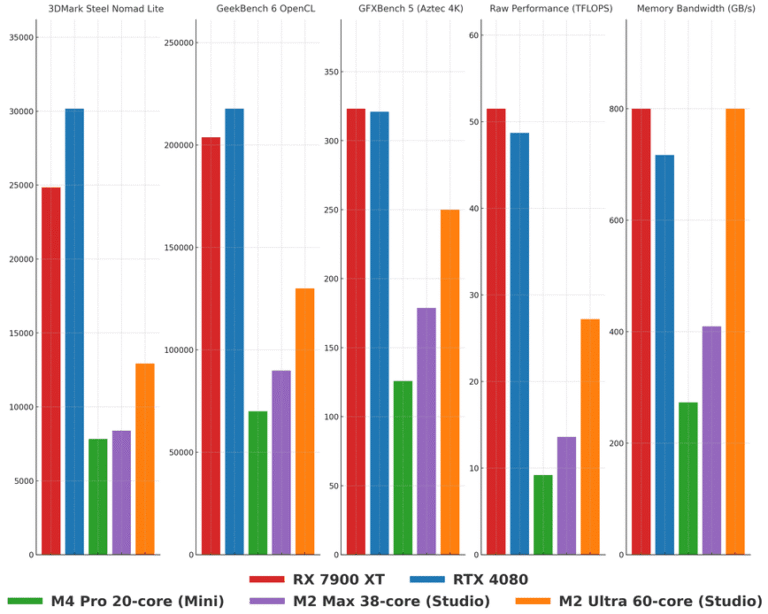
As advancements in machine learning continue to accelerate and evolve, more individuals and small organizations are exploring how to run language models (LLMs) like DeepSeek, LLaMA, Qwen and others on their home servers. This…
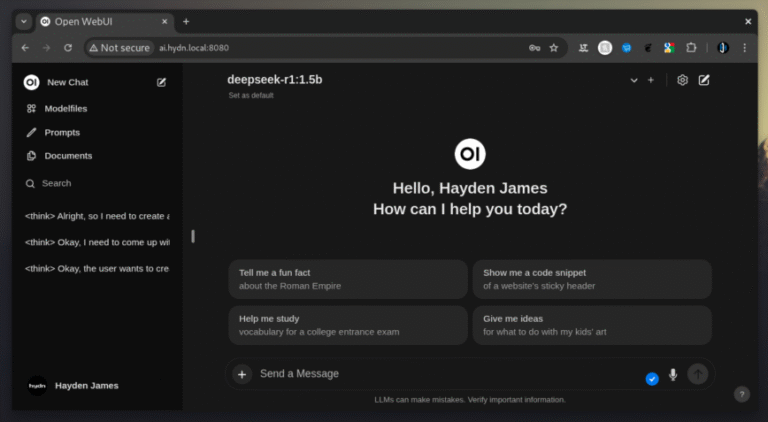
By following this guide, you will be able to successfully self-host your preferred DeepSeek model on a home lab or home office server, harnessing the potential of these AI models in a private and…