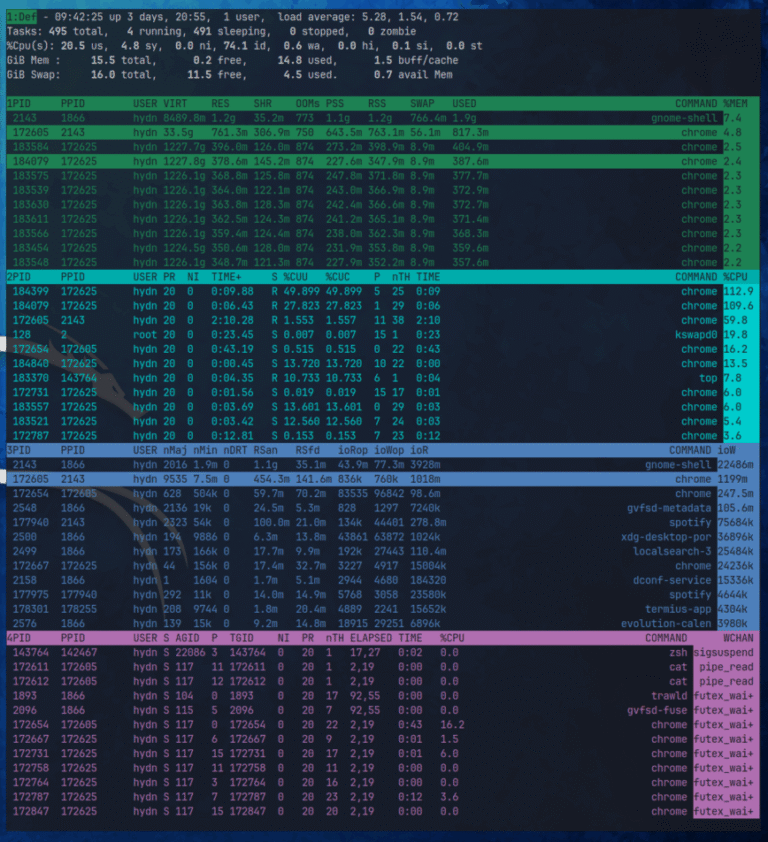
Why Your Linux Server “Looks Idle” but “Feels” Slow
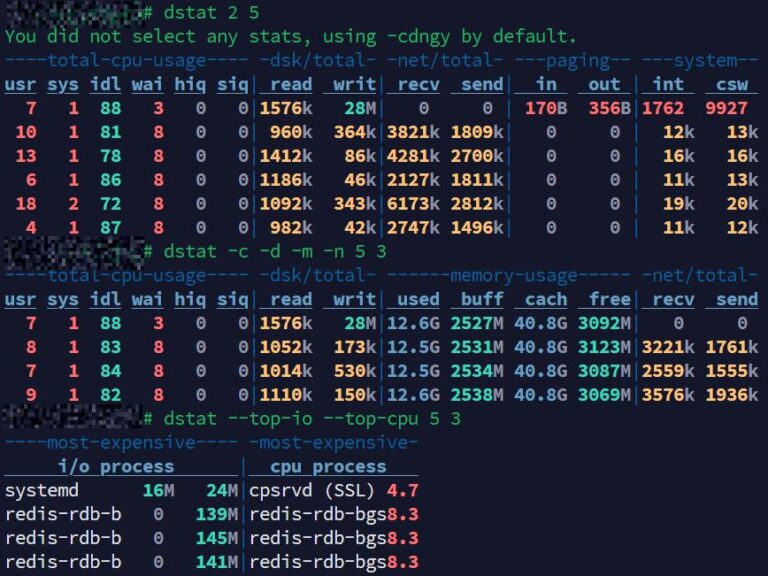
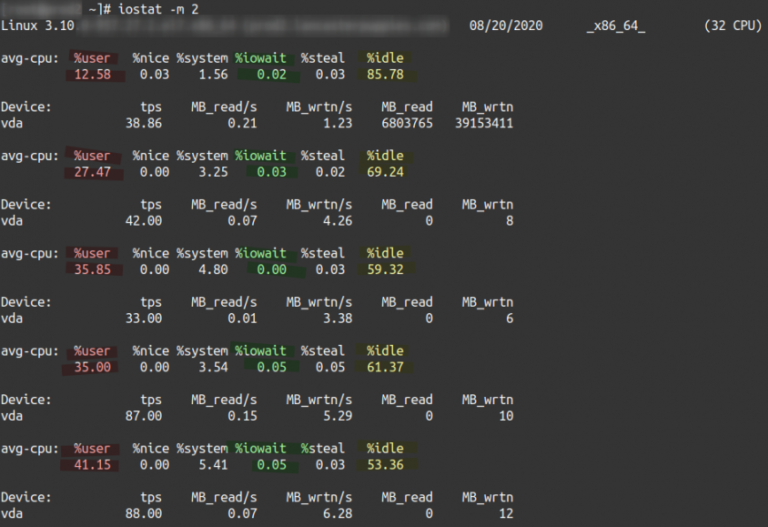
Servers can sometimes appear idle yet still perform sluggishly. This scenario is common across web hosting servers, database servers, VPS or cloud instances, or even containerized workloads. In all mainstream Linux distributions, the…