Amer and Roshan’s System for Bridging the Innovation Gap
Amer: We did some work with Fujifilm – keep in mind this is a company whose major competitor Kodak is used as a cautionary tale of how not to innovate in business schools….

Amer: We did some work with Fujifilm – keep in mind this is a company whose major competitor Kodak is used as a cautionary tale of how not to innovate in business schools….

Injection attacks exploit vulnerabilities in APIs by sending malicious input to manipulate data handling processes. Common types include SQL and XML injection, where attackers insert malicious code through API requests. These attacks often…

There is plenty of talk these days about how generative AI tools can accelerate IT innovation through capabilities like automated code generation. At the same time, there’s a fair amount of concern over…

Behind MigrationWiz stands a team of customer success experts ready to help MSPs build their M&A migration business. The team can offer guidance with MigrationWiz, specifically during the crucial stages of configuration and…

Adopting a multi-cloud strategy enables organizations to leverage the unique strengths of different providers. However, securing the resulting diverse environment can be challenging. Embracing cloud-agnostic security tools can help organizations overcome many of…

By making preconfigured resources available on a self-service basis, platform engineering helps to optimize developer productivity, which in turn benefits the business by increasing the rate at which engineers can build and release…

Proactive Steps: How Tech Companies Can Make Use of Ethical AI For businesses offering innovative solutions to real-world problems, there is a unique opportunity to emerge as voices of reason amid the media…

The idea of automating governance, risk and compliance (GRC) processes to streamline auditing is not exactly new. For some time, many auditing firms have leveraged automation solutions – typically ones that they build…
RealPage delivers a robust SaaS property management software solution that serves a broad spectrum of the real estate market, including multifamily, single-family, commercial, and vacation rental properties. RealPage’s cloud platform is known for…

CYFIRMA confirms that it has found exploit kits for popular software, including Citrix ADC, Microsoft Streaming Service Proxy and PaperCut. However, its research also finds that offering patches after a major CVE breach is only…
Assessing Your Business Needs: To select the most appropriate cloud solution, start by assessing your organization’s specific continuity requirements. Consider factors such as industry demands, company size, and potential risk factors. This will…

eSIMs, or embedded SIMs, are digital SIM cards built directly into a device, allowing users to activate a cellular plan without inserting a physical SIM card. This technology offers flexibility and convenience, particularly…

Looking forward, we can anticipate the development of customized search filters within reverse image search platforms. These filters will allow users to refine their search results based on specific criteria such as image…

Because payment gateways are such a vital component of financial applications, many decide to turn to payment gateway integration services not to risk user’s trust and offer a smooth transaction experience. These services…
Leaseweb delivers affordable dedicated servers with a strong focus on reliability and global reach. Known for its extensive network and flexible server configurations, Leaseweb ensures high performance and security, making it a solid…

Migrating to the cloud can also support sustainability initiatives. Cloud providers often run their data centers more efficiently and use renewable energy sources, thereby reducing the carbon footprint associated with IT operations. In…
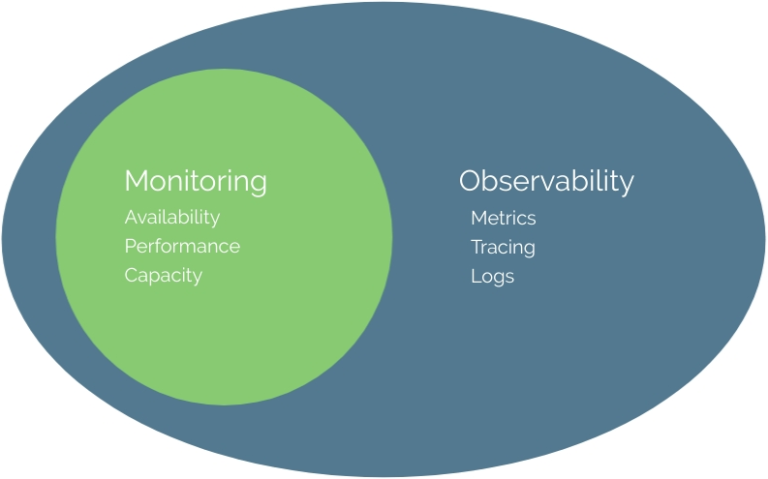
Leading software vendors have completed the expansion from traditional monitoring to full observability. However, there’s still a knowledge gap for customers interested in observability. As a result, some are left feeling a bit…

What Are LLMs? To sum up, the evolution of LLMs and their integration into cloud services represents a step forward in the field of artificial intelligence. By utilizing cloud environments, businesses can accelerate…