Learn Linux: 4 Devices to boost your Linux skills (2025)
Ready to go on a journey that will take your Linux skills to the next level and beyond what theoretical learning can? The devices in this article will give you hands-on experience and…

Ready to go on a journey that will take your Linux skills to the next level and beyond what theoretical learning can? The devices in this article will give you hands-on experience and…
AI is leading in the fight against cyber threats. It is flexible and can detect threats before they hit. The future of virus detection appears promising, even though there are still some problems…

Wes points to an interesting analogy on the information highway—similar to how accountability was managed on the physical highway long ago. He explains, Of the three approaches to the authority necessary for governance:…

Anurag Mehrotra, emphasized at a Dell Tech World event that edge computing will play a pivotal role in handling this influx of data: “The need to process data closer to its source—at the…

Furthermore the launch of Cloudways Autonomous and Cloudways Flexible has expanded the choices to users for managing and expanding their hosting settings. Whether you require scaling for applications, with heavy traffic or favor…

Re-writing or replatforming legacy applications effectively is not easy. Engineers should be confident when working with containers, serverless architecture, and cloud solutions. They should understand the end-to-end process of auditing existing applications, mapping…
AI is also playing a pivotal role in advancing 3D printing in dentistry. AI-driven design software can optimize the creation of dental prosthetics by predicting and adjusting for potential issues, such as material…

Security experts recommend monitoring CPU usage and running temperature diagnostics using tools like Core Temp or HWMonitor. Sudden spikes in CPU activity, especially when the computer is idle, may suggest that cryptojacking scripts…

Copilot’s output is only as good as its input. A unified data environment allows Copilot to be trained on a more extensive set of organizational data. This improves its ability to understand patterns,…

The security risks associated with public and hybrid clouds do not outweigh their benefits. Organizations should not let security concerns deter them from adopting cloud solutions. Instead, they should focus on selecting cloud…

What trends are you seeing in the current M&A landscape, and how do you expect these trends to influence the demand for MSP services in the coming year? How does an MSP ensure…
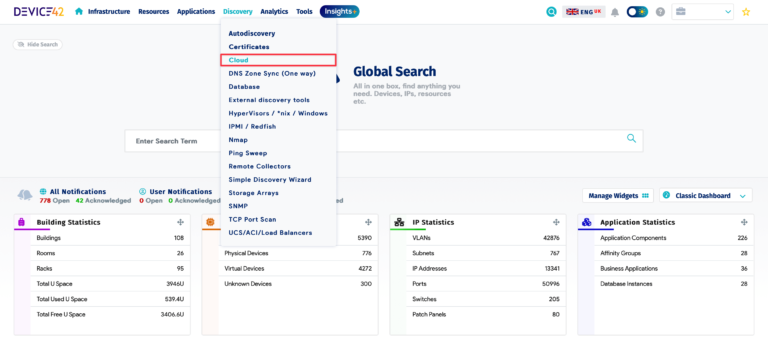
What Is Device42? Through automated tools and real-time insights, Device42 empowers IT teams to manage multi-cloud environments adeptly, enhancing strategic planning and operational resilience. By simplifying intricate processes and providing a centralized overview,…

It has been about two years since generative AI technology exploded onto the radars of most businesses following the release of ChatGPT in late 2022. In that time, the vast majority of organizations…

I’m referring instead to devices that run software that is still actively supported and up-to-date, but that is not fully compatible with modern endpoint management tooling. The result is the ability to manage…

For organizations running mission-critical workloads, utilizing the AWS Enterprise Support plan is essential. The Enterprise tier encompasses all features of the previous plans and additionally offers a 15-minute response time for critical workloads….

In Canada, defendants can request a review of their bail decision under certain conditions, such as a clear legal error or a material change in circumstances. However, challenging an AI-influenced bail decision can…

Why it works: The prompt defines the context (sales team performance) and highlights specific areas (customer relationships, cross-selling) where feedback is needed, ensuring a focused response. Well-designed prompts have five basic characteristics: 1)…
Invest in strong edge computing infrastructure for effective processing and analysis of data from IoT devices. It enables real-time data processing and analytics to be done at the edge, lowering latency, reducing bandwidth…