Immutable Linux Distros: Are They Right for You? Take the Test.
Like the amber in “Jurassic Park,” immutable Linux distros safeguard the core system. Here’s a story about how I, like many of you, have been using Linux for a very long time. I’ve…

Like the amber in “Jurassic Park,” immutable Linux distros safeguard the core system. Here’s a story about how I, like many of you, have been using Linux for a very long time. I’ve…
Nov 27, 2025 Ariffud M. Summarize with: Domain forwarding means pointing a domain you own to another URL, and it can be done even if you don’t necessarily have a website yet. For…
In my earlier article, “Linux: We Need Tiling Desktop Environments,” I advocated for more desktop environments with built-in tiling features. That article sparked valuable discussion in the comments section, and recently the topic…

If you run a home lab long enough, this realization eventually hits you: a lot of your hardware spends more time idle than working. Servers sized for future growth, machines you planned to…

Dec 12, 2025 Ariffud M. Summarize with: When Anthropic announced Agent Skills, my first thought was: “So… are these just prompts saved in a folder? Is this a real feature or clever marketing?”…
ThinkPad laptops have become synonymous with reliability and innovation in the tech world. As a Linux enthusiast, you understand the importance of selecting the right laptop for your projects, work, and other professional…
As we stand on the brink of 2024, 2025, 2026 AI has already established itself as an essential collaborator in the workplace. The relationship between humans and AI is growing, moving beyond just…
“A more targeted list that includes 50 server and observability solutions for 2026” Back in 2014, I compiled a list of top server and application performance monitoring solutions. Sharing that list publicly was a great…
Today’s software applications require developers, testers, and SysAdmins to work together (DevSecOps) more seamlessly than ever before. A single line of code or poorly configured service can negatively impact your application’s performance, causing…
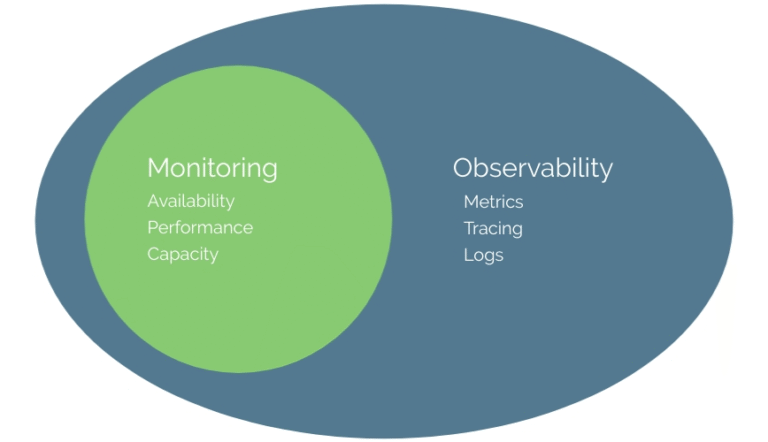
Previously we’ve covered the future of APM (application performance monitoring) and the expansion of APM into observability. Followed by the race between software vendors to define observability. Most recently, we looked at the evolution…
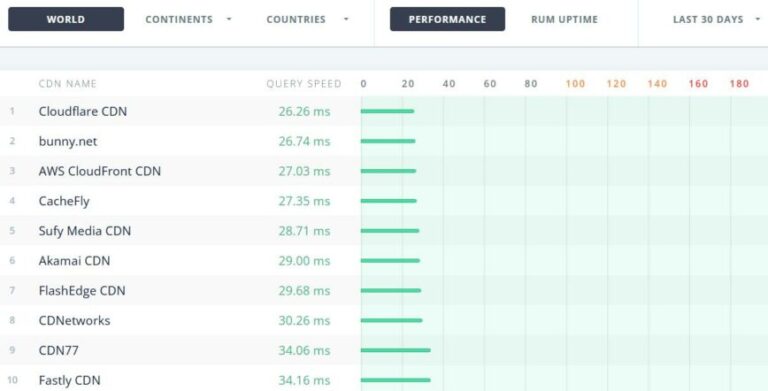
A content delivery network, also referred to as a content distribution network (CDN), is a geographically distributed network of data centers containing proxy servers. CDN providers serve internet content, including web objects (text, graphics, and scripts), downloadable…
Nov 05, 2025 Summarize with: WordPress is an open-source content management system (CMS) that provides the underlying architecture and core functionality for your website. When using WordPress without a page builder, you primarily…
Oct 31, 2025 Ariffud M. Summarize with: Most people transfer a domain to get better renewal pricing, consolidate services with their hosting provider, or escape poor customer support. To transfer your domain to…
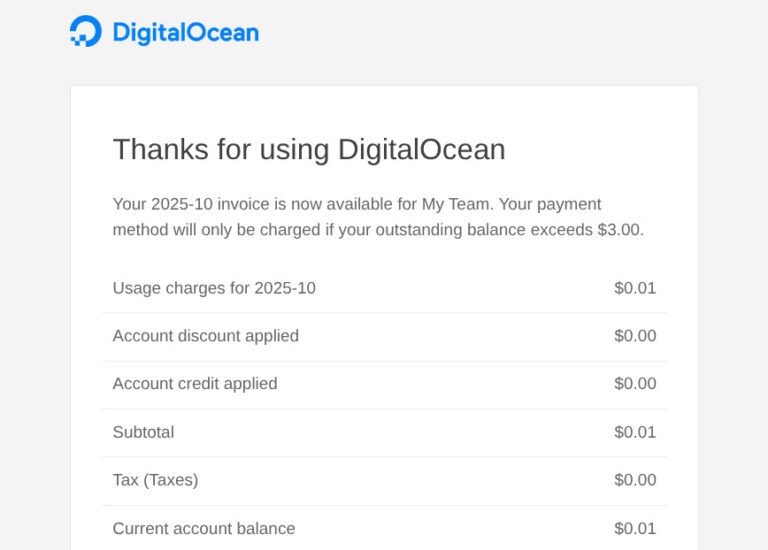
There are three kinds of emails that can ruin a quiet Saturday: a security warning, an outage alert, and, apparently, a repeat reminder that you owe a cloud provider one cent, yes, $0.01….
I’ll admit, I hesitated a bit before writing this post. The whole point of this linuxblog.io and linuxcommunity.io forum is to bring together like-minded Linux users and professionals so we can troubleshoot, share…
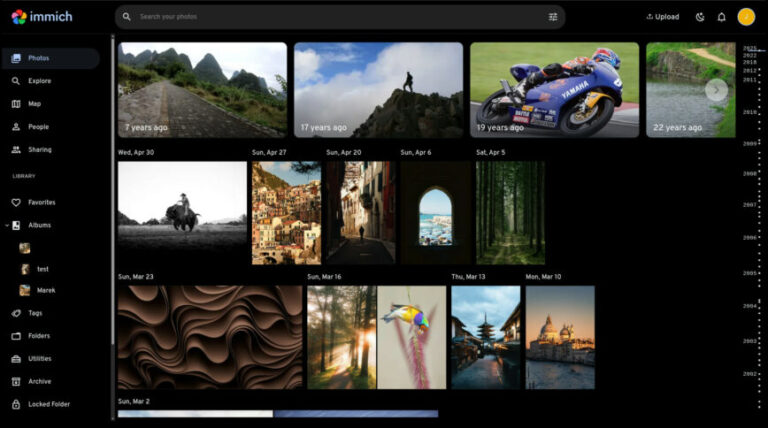
Tonight, I stumbled upon Immich, a self-hosted photo and video management solution, and I’m blown away. With Immich, you can back up and organize all your photos and videos on your own server….

This article is inspired by our LinuxCommunity.io forum discussion thread (thanks to users @tmick and @shybry747 for the feedback). Let’s walk through what Podman is and how to use it as a Docker…

Docker is a platform for packaging and running applications in isolated units called containers. Each container bundles an application together with its libraries and dependencies, sharing the host’s Linux kernel instead of a…