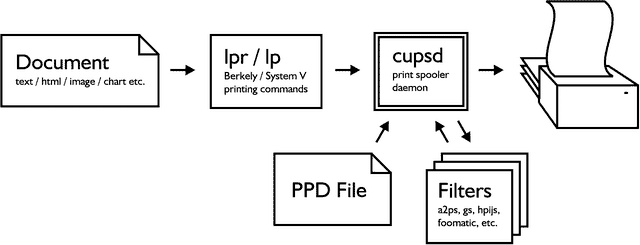
Best low-memory Linux Server Distros for < 1GB deployments
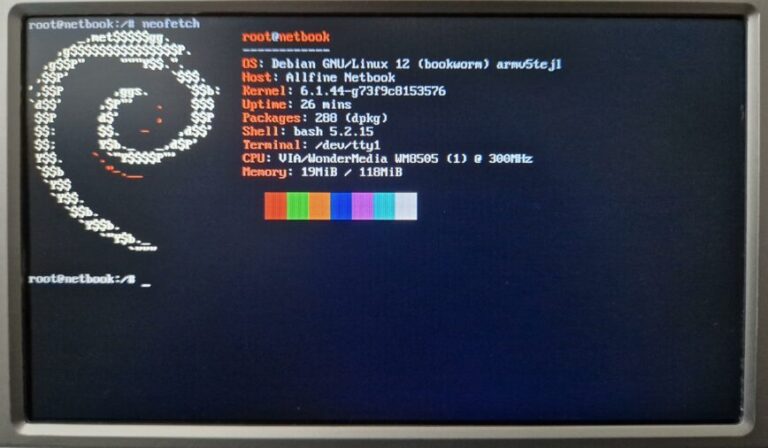
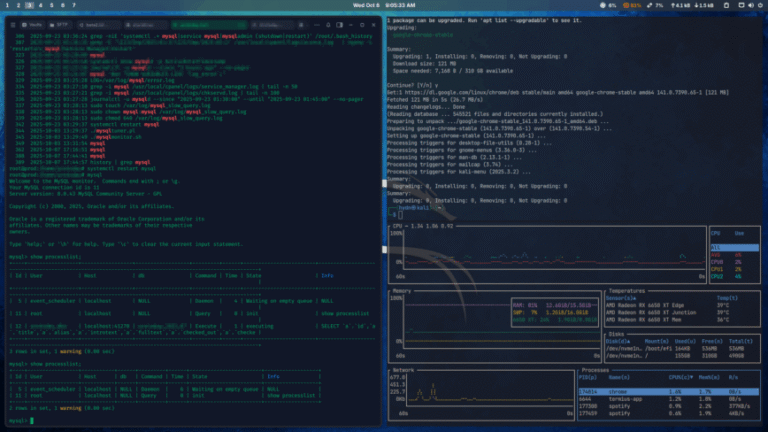
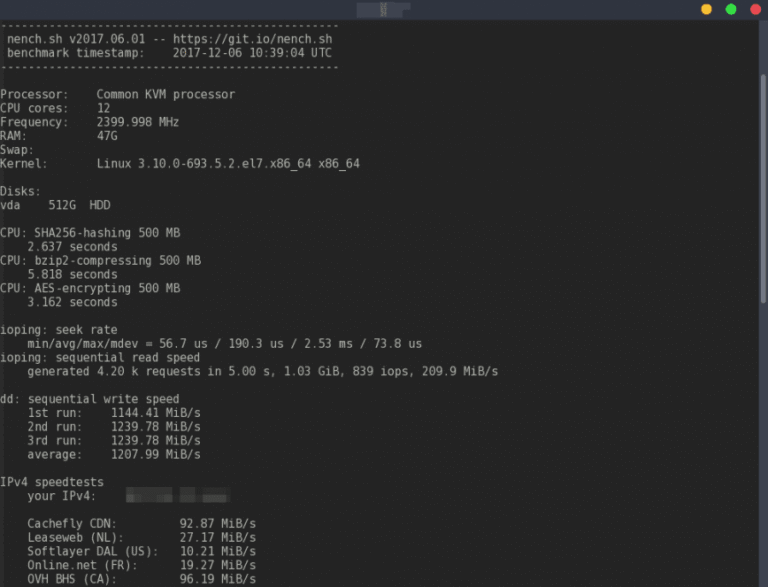
Running Linux servers on under 1 GB of RAM (think 512 MB or even 256 MB) can be challenging, but it’s absolutely feasible with the right distro choice. I’ve found that using ultra-lightweight…