DigitalOcean is chasing me for $0.01: What it taught me about automation
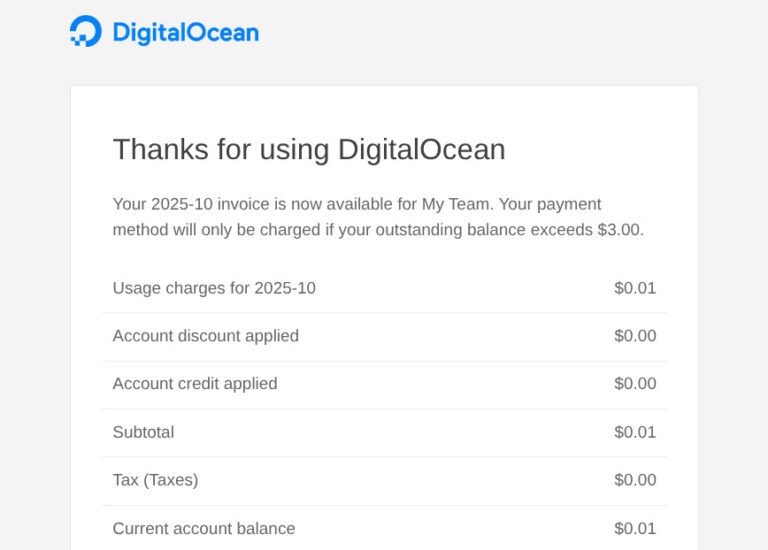
There are three kinds of emails that can ruin a quiet Saturday: a security warning, an outage alert, and, apparently, a repeat reminder that you owe a cloud provider one cent, yes, $0.01….