Raspberry Pi Not Booting: How to Repair Micro SD Card
I have a Raspberry Pi 4 (2 GB RAM) that’s been running my UniFi Network Controller for about four years without issues. Yesterday it was unresponsive and would not boot at all. The…
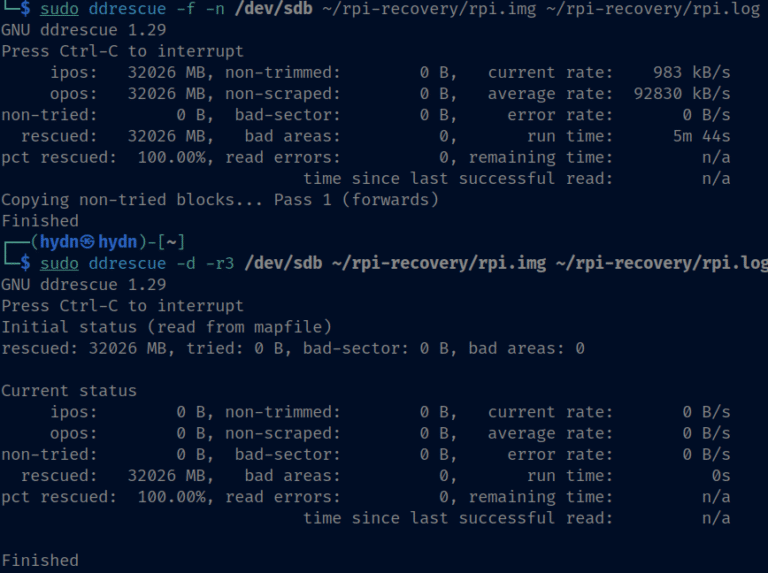
I have a Raspberry Pi 4 (2 GB RAM) that’s been running my UniFi Network Controller for about four years without issues. Yesterday it was unresponsive and would not boot at all. The…
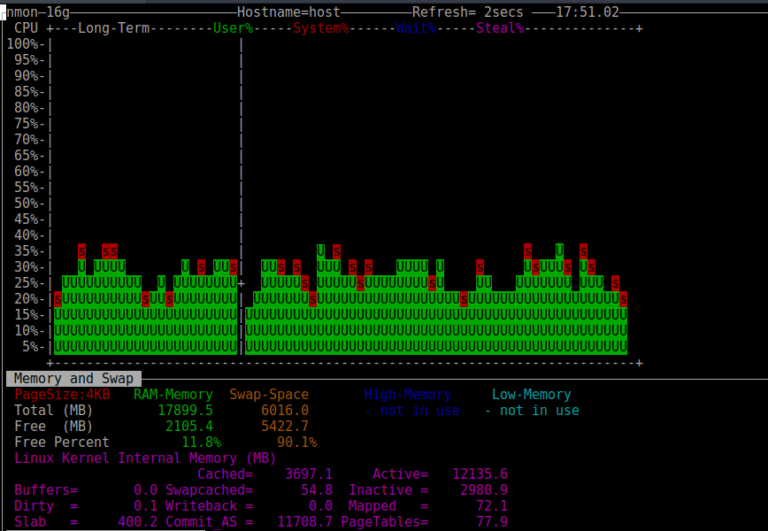
In the previous article, we looked at how swap space, particularly swapping, can severely slow down Linux performance. We then tweaked Linux kernel parameters to better use server memory and avoid heavy swapping….
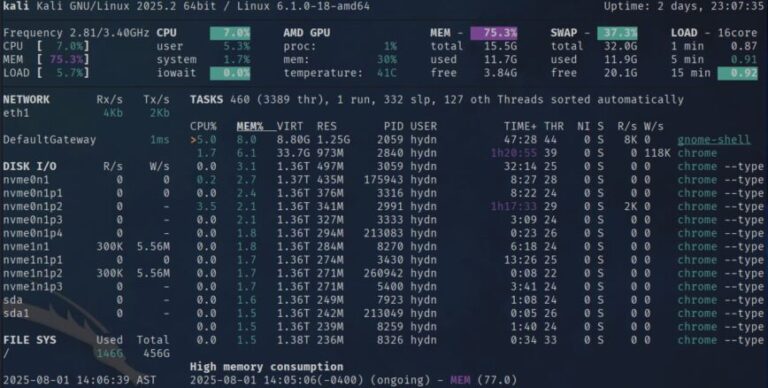
Rule of thumb / TL;DR:If your system only uses swap occasionally and keeping swap demand within ~20–30% of your physical RAM as zram is enough, ZRAM is the simpler and more effective option….
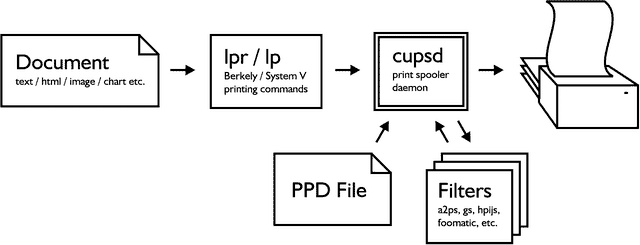
If you are looking for Linux compatible printers, in this article, you will find printers that seamlessly integrate with Linux operating systems. We’ll explore a selection of high-quality printers from various brands, along…

This article focuses on the benefits of rolling network racks for established or expanding home networks. If you’re looking for a comprehensive guide to building your first home lab, read my Home Lab…

A few weeks ago, I had the opportunity to attend a small trade show, which got me thinking (again) about how AI is shaping the future of work. I wanted to share a…
This post explores over 30 of the best Linux terminal emulators, each with unique features and functionality, catering to different types of users. This list showcases the versatility and evolution of terminal emulators…

Last week I walked into an empty 5 × 4 ft storage room. By the end of the week, that blank space held a fully functional network core designed to keep a small…
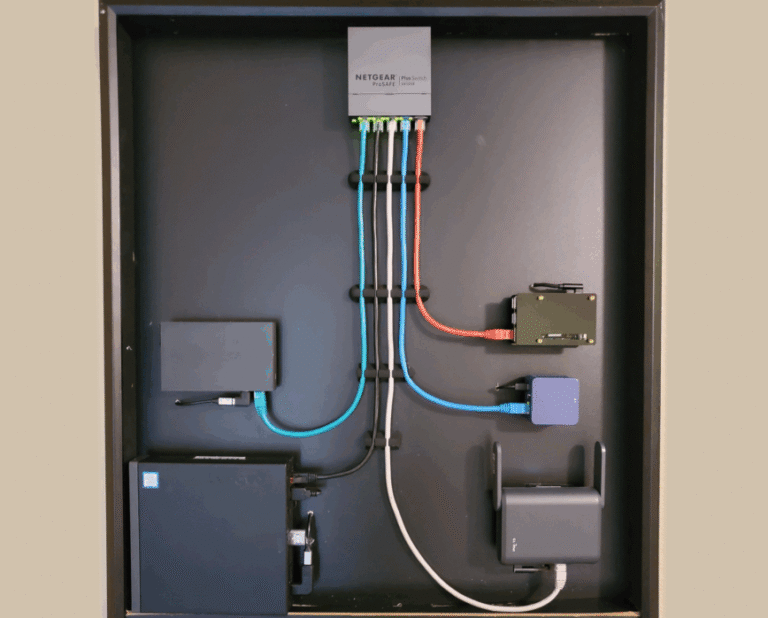
Choosing the right network switch is essential for building a reliable home network, home lab, or small‑office setup. The process can feel deceptively simple until slow file transfers or unexpected upgrade costs remind…

Choosing a switch can feel deceptively simple, until slow file transfers, port shortages, and similar unexpected upgrade costs remind you otherwise. Before you click “Buy,” it helps to step back and look at…
This article is a follow-up to the previous 90 Linux Commands frequently used by Linux Sysadmins post. Every week, as time allows, I will publish articles on the 90 commands geared toward Linux sysadmins and…
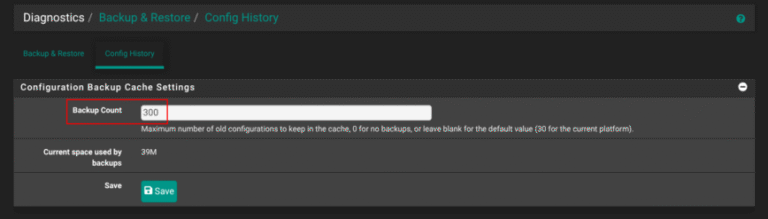
Just installed pfSense? Before diving into VLANs, firewall rules, or VPN tunnels, take a few minutes to lock in these essential setup changes. These quick tweaks will boost security, improve reliability, and prevent…
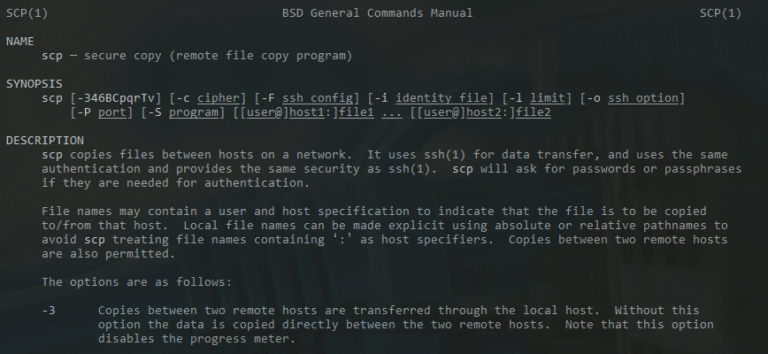
This post includes SCP examples. SCP or secure copy allows the secure transferring of files between a local host and a remote host or between two remote hosts. It uses the same authentication…
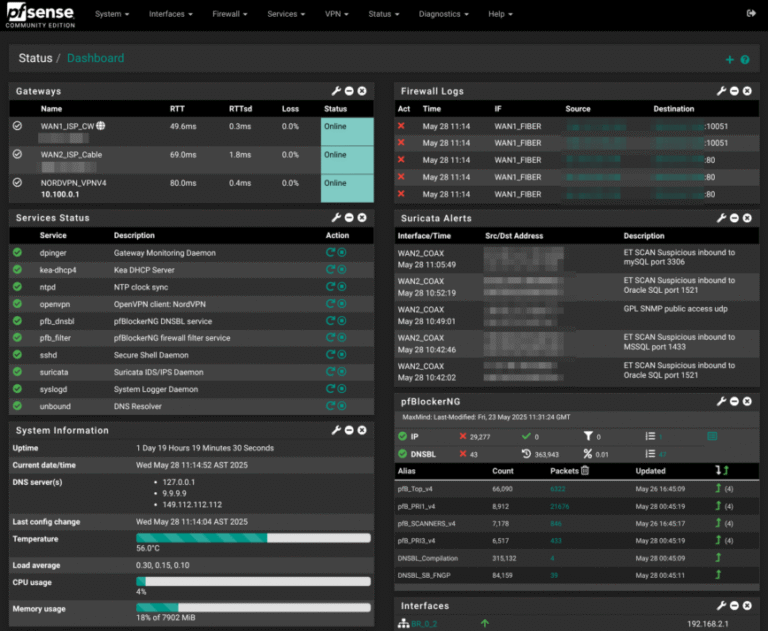
Let’s pick up right where Part 1 left off: pfSense Firewall Appliance Unboxing. This isn’t a quick-start guide. It’s my logbook from weeks of fine-tuning pfSense. Weeks, not years, so follow along and…
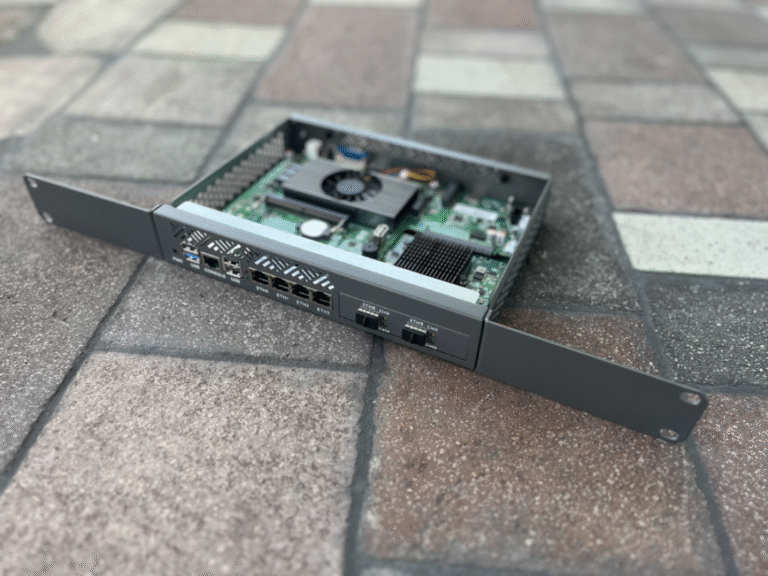
For the past three years, I’ve been putting off an upgrade to my network’s firewall. During that time, I was balancing multiple priorities: maintaining uptime with multiple ISPs, managing VPN performance limitations, and…

The sudo command in Linux is one of the most important and widely used commands for managing system permissions. It allows you to run a command as the superuser, giving you elevated privileges…
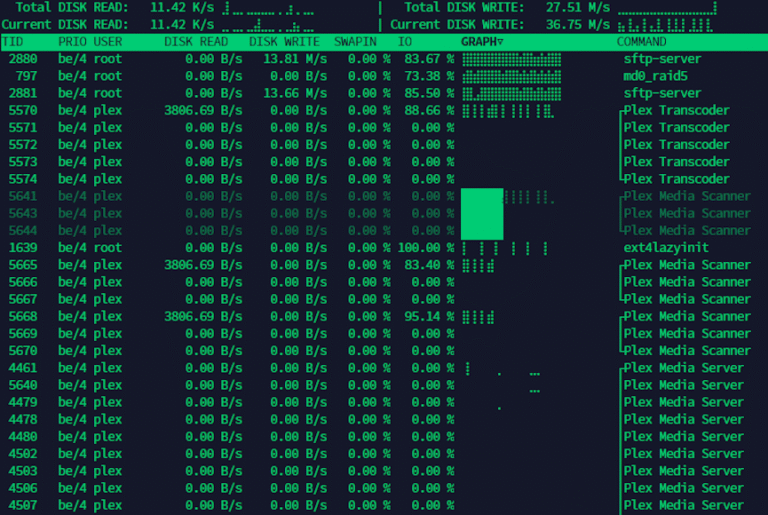
This iotop command guide follows my previous 90 Linux Commands frequently used by Linux Sysadmins article. As time allows, I will continue to publish articles on the 90+ commands geared toward Linux sysadmins…
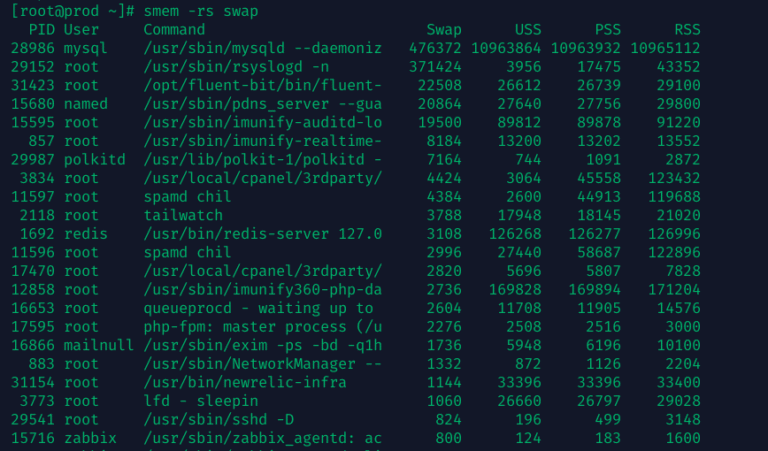
If you’ve ever looked at your server and wondered why it’s using swap even though plenty of RAM is available, you’re not alone. This is a common scenario on Linux systems, and it…