InvGate Insight also allows you to automate multiple ITAM tasks within the platform. For instance, you could use health rules to receive alerts whenever an asset needs attention. Or you could use custom notificationssmart tags to quickly identify unauthorized software installations in your organization.
InvGate addresses this need with key functionalities such as:
By Gary Bernstein
In particular, uses can:
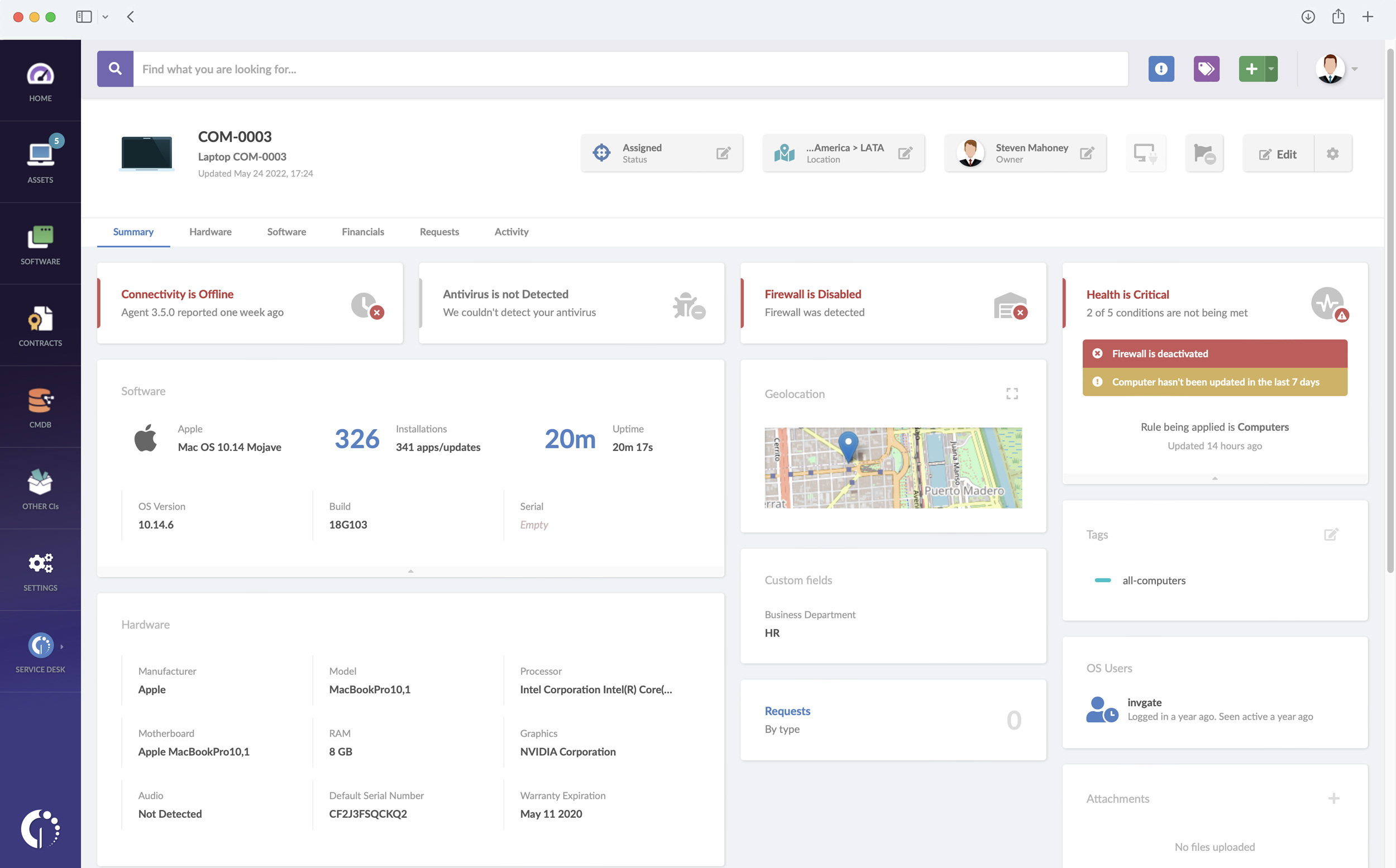
InvGate Insight’s performance as IT Asset Management software
With it, organizations can:
Audits and compliance
By choosing InvGate, organizations can achieve superior IT Infrastructure Management, boost service reliability, and make informed strategic decisions without the hassle of lengthy implementations or high consulting costs.
Their design is based on no-code capabilities that provide users with autonomy to adapt and grow without the burden of prolonged implementations or exorbitant consulting fees. InvGate’s Service Management and Asset Management solutions are designed to streamline operations, ensuring efficiency and flexibility for businesses of all sizes.
- Automate the review and verification of IT assets to ensure they comply with established policies and regulations.
- Identify any discrepancies, and promptly address non-compliance issues.
- Save money by identifying and managing unused or underutilized software licenses.
- Build reports to demonstrate compliance during external audits, reduce non-compliance risks, and enhance overall IT governance.
IT security
Ensuring compliance with regulatory requirements and internal standards is critical to IT Asset Management. InvGate Insight’s Software Audits and Compliance feature is designed to help organizations meet these demands effectively.
With over 15 years of experience, InvGate develops essential tools that empower IT teams to support every department within a company. Currently present in more than 60 countries – and with renowned companies such as the U.S. Army, Collins Aerospace, NASA, PWC, and Toyota as clients – InvGate provides two stand-alone though highly integrated products: an ITSM (IT Service Management) and ITAM (IT Asset Management) solution.
- Implement access controls, encryption, and continuous monitoring of IT assets.
- Receive alerts and automated responses to potential security issues.
- Maintain a secure and resilient IT infrastructure.
Full Lifecycle Management
Plus, it gives users robust security measures and automation capabilities to streamline processes, reduce errors, and enhance overall efficiency.
In addition, its native integration with InvGate Service Desk expands Insight’s capabilities to include workflow automation for various tasks, such as user provisioning, software updates, and system diagnostics. This reduces manual intervention and minimizes human errors. Users can link assets to tickets by connecting the two to streamline the support process.
These capabilities are essential for enhancing security by ensuring that all devices within an organization’s network are uniformly updated and protected against vulnerabilities.
- Inventory Management, which effectively traces hardware and software assets.
- Finance Management that optimizes the spending and budgeting on resources related to IT.
- Compliance Management to guarantee the continued observance of standards and regulations.
- A wide range of integrations with other IT systems to ensure flexibility, data accuracy, and efficiency.
Such a comprehensive approach to Asset Management improves operational efficiencies and supports strategic decision-making based on detailed insight into asset utilization, performance, and costs.
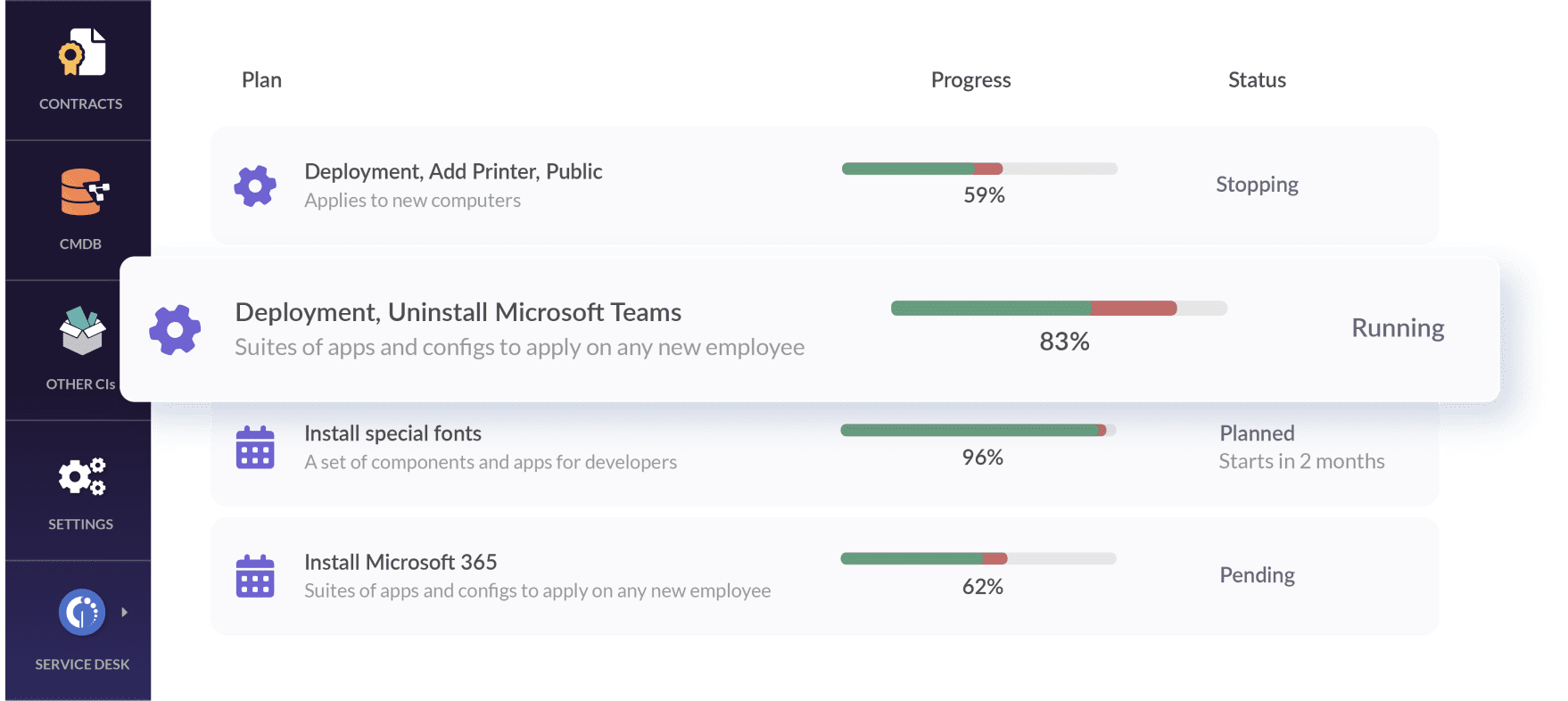
Software deployment for internal policies
While InvGate Service Desk offers all the necessary features to build a state-of-the-art service desk (including Ticket Management, workflows, self-service options, and analytics), InvGate Insight addresses all ITAM-related needs.
InvGate’s software deployment feature allows for batch installation, configuration, and software updates across multiple devices. You can deploy software through the dashboard (built with a no-code approach) or by using scripts for more custom configurations.
In conclusion, InvGate’s ITAM solution, Insight, is a game-changer for organizations looking to optimize their IT operations. The no-code flexibility allows for seamless adaptation and growth, while comprehensive features like the CMDB, software deployment, and automated audits ensure thorough Asset Management and compliance.
Automation
IT Asset Management software is designed to manage and optimize IT assets at every level within an organization. This genre of solutions ensures that businesses can track and manage the full Lifecycle Management of physical and digital assets, from acquisition to disposal.
Protecting IT environments from threats and vulnerabilities is crucial for any organization. InvGate Insight’s Security feature equips organizations with the tools they need to safeguard their IT environments, ensuring both regulatory compliance and the protection of critical assets.
Conclusion
This leads to improved operational efficiency, faster resolution of IT issues, and higher service reliability, ultimately contributing to a more productive and agile IT environment.
In general, this platform ensures that IT security standards are followed and gives centralized Asset Management in multiple locations. But let’s take a closer look at the different situations in which it can be useful.
At its core, Insight is a comprehensive ITAM suite designed for visibility and control of the IT infrastructure. Its key features include a Configuration Management Database (CMDB) that maps IT infrastructures, a Software Compliance module for License Management and optimization, software deployment capabilities, remote access, Financial Management, asset monitoring to manage software and hardware throughout their lifecycle, and customizable dashboards and reports to monitor performance.
You can use ITAM software for multiple purposes. For instance, it is helpful to perform internal audits, stay compliant with regulatory requirements, ensure a secure perimeter, and handle all your IT assets, from acquisition to disposal.



