After 10 Yrs of Linux, I Switched to Windows. What next?
As a Linux user, you might wonder why someone would ever want to replace it with Windows. Be nice! It’s always good to see how other operating systems work. And being proficient in…
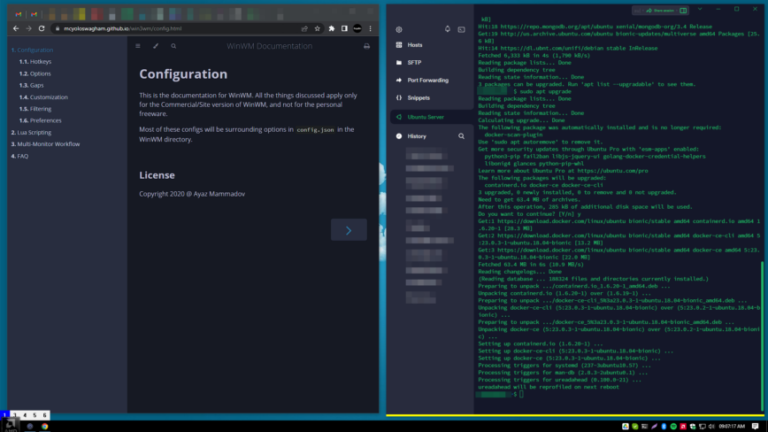
As a Linux user, you might wonder why someone would ever want to replace it with Windows. Be nice! It’s always good to see how other operating systems work. And being proficient in…

Anurag Mehrotra, emphasized at a Dell Tech World event that edge computing will play a pivotal role in handling this influx of data: “The need to process data closer to its source—at the…

Furthermore the launch of Cloudways Autonomous and Cloudways Flexible has expanded the choices to users for managing and expanding their hosting settings. Whether you require scaling for applications, with heavy traffic or favor…
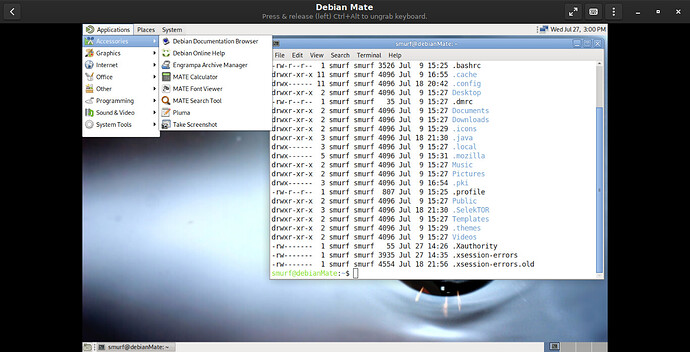
So I’m not in love with Gnome 3, I actually use Gnome Classic as a desktop. I’ve been having some issues with Classic view as well. So I went on an exploration trip…

Re-writing or replatforming legacy applications effectively is not easy. Engineers should be confident when working with containers, serverless architecture, and cloud solutions. They should understand the end-to-end process of auditing existing applications, mapping…
Oct 15, 2024 Ariffud M. Ollama is an open-source tool that runs large language models (LLMs) directly on a local machine. This makes it particularly appealing to AI developers, researchers, and businesses concerned…

Security experts recommend monitoring CPU usage and running temperature diagnostics using tools like Core Temp or HWMonitor. Sudden spikes in CPU activity, especially when the computer is idle, may suggest that cryptojacking scripts…
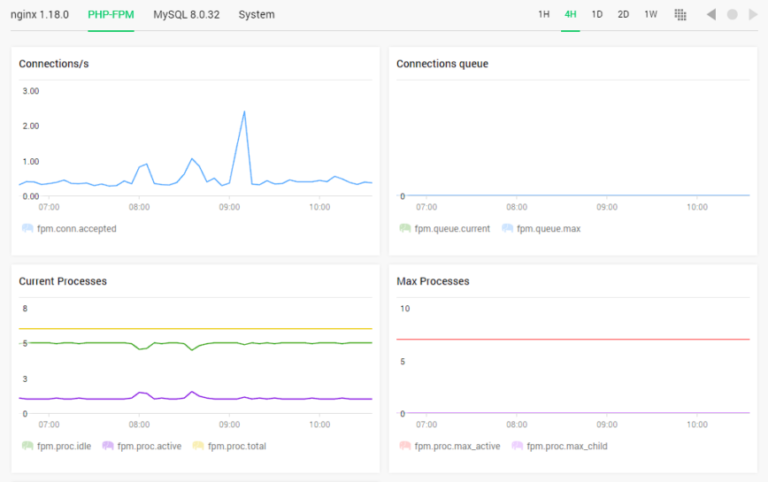
As one of the most widely used scripting languages for web development, PHP is known for its flexibility and ease of use. However, with complex applications and increasing traffic, PHP performance can sometimes…

Copilot’s output is only as good as its input. A unified data environment allows Copilot to be trained on a more extensive set of organizational data. This improves its ability to understand patterns,…

PITTSBURGH, October 15, 2024 (Newswire.com) – River Point Technology (RPT), an award-winning cloud consulting, training, and enablement provider, is thrilled to announce that they have been named HashiCorp’s Americas SI Partner of the Year…
Oct 14, 2024 Many digital business owners rely on DevOps to improve productivity through automation and collaboration. They commonly use a Git platform like GitLab to create a centralized repository, version control system,…

The security risks associated with public and hybrid clouds do not outweigh their benefits. Organizations should not let security concerns deter them from adopting cloud solutions. Instead, they should focus on selecting cloud…
Oct 02, 2024 Valentinas C. Ollama is an open-source platform that lets you run fine-tuned large language models (LLMs) locally on your machine. It supports a variety of popular LLMs, including Llama 2,…

What trends are you seeing in the current M&A landscape, and how do you expect these trends to influence the demand for MSP services in the coming year? How does an MSP ensure…
What Is Device42? Through automated tools and real-time insights, Device42 empowers IT teams to manage multi-cloud environments adeptly, enhancing strategic planning and operational resilience. By simplifying intricate processes and providing a centralized overview,…

Oct 04, 2024 If SiteGround no longer meets your website’s needs, it might be time to switch to a new hosting provider. Migrating can boost performance, enhance user experience, and provide stronger security…

It has been about two years since generative AI technology exploded onto the radars of most businesses following the release of ChatGPT in late 2022. In that time, the vast majority of organizations…
Oct 01, 2024 Jordana A. If your current hosting can no longer support your needs, it’s time to switch web hosts. Doing so helps enhance web performance, provide a consistent user experience, and…